I am not feeling great today, the British public has just shown what a bunch of idiots they are and have voted to leave the EU. Absolutely crazy. But, despite feeling despondent, I need to finish off the IPS.
Today will be pretty quick. The goal is to get the WLC talking to the IPS. Why are we doing this, apart from "just because we can"?
The idea is that we will have traffic that may not be going through the IPS, predominantly Wifi traffic. The IPS is a clever thing and can use the signature-definition rules to create lists of IP addresses we "shun". So we get the benefits of the IPS, even when on the Wifi network.
Creating a shun list looks a bit like this:
The next step is to set up a user for the WLC on the IPS. I am cribbing from this Cisco doc by the way!
Click on "New" in the top right-hand corner and enter the details:
If you are wondering how to get the SHA fingerprint, that comes from the IPS:
We should be able to pull data from the IPS now - if it worked:
Of course, this is only as good as the stability of the IPS, so it quickly craps out:
The point has been proven, though.
The IPS is kind of pissing me off. It keeps needing to be reset, which is just wasting time. But I think we can leave it there.
It's time to move on and look at VPNs.
Today will be pretty quick. The goal is to get the WLC talking to the IPS. Why are we doing this, apart from "just because we can"?
The idea is that we will have traffic that may not be going through the IPS, predominantly Wifi traffic. The IPS is a clever thing and can use the signature-definition rules to create lists of IP addresses we "shun". So we get the benefits of the IPS, even when on the Wifi network.
Creating a shun list looks a bit like this:
IPS(config)# service signature-definition sig1 Editing new instance sig1. IPS(config-sig)# IPS(config-sig)# signatures 64999 0 IPS(config-sig-sig)# alert-severity high IPS(config-sig-sig)# engine atomic-ip IPS(config-sig-sig-ato)# event-action ? produce-alert produce-verbose-alert deny-attacker-inline deny-connection-inline deny-packet-inline log-attacker-packets log-pair-packets log-victim-packets request-block-connection request NAC to shun this connection request-block-host request NAC to shun this attacker host request-snmp-trap reset-tcp-connection deny-attacker-victim-pair-inline deny-attacker-service-pair-inline IPS(config-sig-sig-ato)# event-action request-block-host IPS(config-sig-sig-ato)#I won't be using this one, though, I will be editing the existing signature we set up in the previous post.
IPS(config)# service signature-definition sig0
IPS(config-sig)# signatures 60101 0
IPS(config-sig-sig)# engine atomic-ip
IPS(config-sig-sig-ato)# event-action produce-verbose-alert
IPS(config-sig-sig-ato)# event-action request-block-host
IPS(config-sig-sig-ato)# exit
IPS(config-sig-sig)# show settings
sig-id: 60101
subsig-id: 0
-----------------------------------------------
alert-severity: high default: medium
sig-fidelity-rating: 75
promisc-delta: 0
sig-description
-----------------------------------------------
sig-name: My Sig
sig-string-info: My Sig Info
sig-comment: Sig Comment
alert-traits: 0
release: custom
sig-creation-date: 20000101
sig-type: Other
-----------------------------------------------
engine
-----------------------------------------------
atomic-ip
-----------------------------------------------
event-action: request-block-host default: produce-alert
fragment-status: any
specify-l4-protocol
-----------------------------------------------
yes
IPS(config-sig-sig)# exit
IPS(config-sig)# exit
Apply Changes?[yes]: yes
IPS(config)#
The rest of the settings are the same as the previous post, so I have truncated the output.The next step is to set up a user for the WLC on the IPS. I am cribbing from this Cisco doc by the way!
IPS(config)# service network-access
IPS(config-net)# user-profile vWLC
IPS(config-net-use)# username vWLC
IPS(config-net-use)# password
Enter password[]: *****
Re-enter password: *****
IPS(config-net-use)# enable-password
Enter enable-password[]: *****
Re-enter enable-password: *****
IPS(config-net-use)# show settings
profile-name: vWLC
-----------------------------------------------
enable-password:
password:
username: vWLC default:
-----------------------------------------------
IPS(config-net-use)# exit
IPS(config-net)# exit
Apply Changes?[yes]: yes
IPS(config)#
Moving on to the WLC, we head to Security > Advanced > CIDS.Click on "New" in the top right-hand corner and enter the details:
If you are wondering how to get the SHA fingerprint, that comes from the IPS:
IPS# sh tls fingerprint MD5: 34:F0:0A:8B:F5:4F:E0:89:2A:99:0C:8F:A1:22:64:CF SHA1: 8F:4E:BF:26:8C:62:8E:5E:C3:80:F4:FD:D4:15:FC:1C:1A:46:80:DF IPS#This then goes on our list:
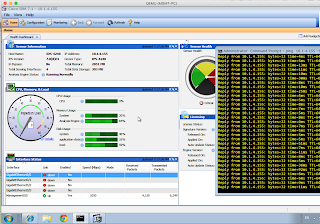
We should be able to pull data from the IPS now - if it worked:
(Cisco Controller) >debug wps cids enable (Cisco Controller) >*osapiBsnTimer: Jun 24 13:06:27.592: cidsSdeeCallback is called *cids-cl Task: Jun 24 13:06:27.592: cidsProcessSdeeQuery: ip=10.1.4.155,port=443 state=1 interval=60 *cids-cl Task: Jun 24 13:06:27.592: cidsQuerySend: https://10.1.4.155:443/cgi-bin/transaction-server?command=getShunEntryList *cids-cl Task: Jun 24 13:06:27.592: curlHandle is 0xe44db58 *cids-cl Task: Jun 24 13:06:27.592: Perform on curlHandle 0xe44db58 ... *cids-cl Task: Jun 24 13:06:27.624: Response code is 7: *cids-cl Task: Jun 24 13:06:27.624: Curl Error! Response 7:couldn't connect to hostThis is going to cause issues with IDM, but let's try anyway:
IPS# conf t IPS(config)# service web-server IPS(config-web)# enable-tls true IPS(config-web)# port 443 IPS(config-web)# exit Apply Changes?[yes]: yes IPS(config)# exit IPS# (Cisco Controller) >debug wps cids enable (Cisco Controller) >*osapiBsnTimer: Jun 24 13:13:32.405: cidsSdeeCallback is called *cids-cl Task: Jun 24 13:13:32.410: cidsProcessSdeeQuery: ip=10.1.4.155,port=443 state=1 interval=60 *cids-cl Task: Jun 24 13:13:32.410: cidsQuerySend: https://10.1.4.155:443/cgi-bin/transaction-server?command=getShunEntryList *cids-cl Task: Jun 24 13:13:32.410: curlHandle is 0xe44db58 *cids-cl Task: Jun 24 13:13:32.410: Perform on curlHandle 0xe44db58 ... *cids-cl Task: Jun 24 13:13:32.538: ssl_sensor_verify_callback: verifying cert from sensor *cids-cl Task: Jun 24 13:13:32.538: Cert fingerprint verified *cids-cl Task: Jun 24 13:13:32.831: Response code is 0: *cids-cl Task: Jun 24 13:13:32.831: Add 123.123.123.123 from local sensor 10.1.4.155 to shun-list *cids-cl Task: Jun 24 13:13:32.831: xmlDoc buffer freed *cids-cl Task: Jun 24 13:13:32.831: Parser cleaned *cids-cl Task: Jun 24 13:13:32.831: 0 cids-update groupcast messages sentLooks better. We can even see a manually created entry I made earlier on the IPS:
Of course, this is only as good as the stability of the IPS, so it quickly craps out:
The point has been proven, though.
The IPS is kind of pissing me off. It keeps needing to be reset, which is just wasting time. But I think we can leave it there.
It's time to move on and look at VPNs.