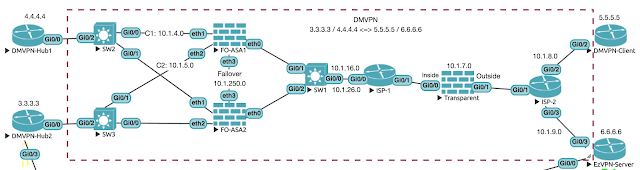
I am a little way away from setting up DMVPN, the IP addressing is all set, but I still need to configure OSPF across the multi-context ASA, the ISP routers and the IOS routers at each side. We also need to permit some traffic through the transparent firewall. Most of the work in this post is concerned with OSPF, but we will also cover some more NAT commands as well.
We are working on this part of the topology now:
Let's start by setting up some default routes on the contexts:
How do we fix this then? Should we permit everything through the firewalls or use NAT? If we NAT the networks behind the multi-context firewalls, then we lose the ability to have incoming traffic, well, if we overload, or PAT we do. Let's look at it another way; what do we need to achieve?
Ideally, all of the loopbacks should have connectivity, so we can exempt these like we did when setting up the IPSec between RTD-ASA and DMVPN-Hub2. This is important as the DMVPN clients will be peering to these addresses, but we could make it a bit more interesting by NAT'ing these address to external addresses and achieve the same result that way.
OK, so here's the plan:
Annoyingly I can't really use the range command to cover all of the subnets, as the 10.1.4.0/24 network belongs to a different context, so let's see what we can do instead. Object-groups would be a good thing here (note the change in context):
Ths now means we should be able to set up DMVPN in the next post.
We are working on this part of the topology now:
Let's start by setting up some default routes on the contexts:
FO-ASA# changeto con C1 FO-ASA/C1# conf t FO-ASA/C1(config)# route outside 0 0 10.1.16.1 FO-ASA/C1(config)# FO-ASA/C1(config)# changeto con C2 FO-ASA/C2(config)# FO-ASA/C2(config)# route outside 0 0 10.1.26.1 FO-ASA/C2(config)# FO-ASA/C2(config)#We can add a bit of routing:
FO-ASA/C1(config)# router ospf 16 FO-ASA/C1(config-router)# router-id 10.1.16.254 FO-ASA/C1(config-router)# network 10.1.4.0 255.255.255.0 area 0 FO-ASA/C1(config-router)# exit DMVPN-Hub1(config)#router ospf 16 DMVPN-Hub1(config-router)#router-id 4.4.4.4 DMVPN-Hub1(config-router)#network 10.1.4.0 255.255.255.0 area 0 DMVPN-Hub1(config-router)#network 4.4.4.4 255.255.255.255 area 0 DMVPN-Hub1(config-router)# FO-ASA/C1(config)# changeto con C2 FO-ASA/C2(config)# router ospf 26 FO-ASA/C2(config-router)# router-id 10.1.26.254 FO-ASA/C2(config-router)# network 10.1.5.0 255.255.255.0 area 0 FO-ASA/C2(config-router)# DMVPN-Hub2(config)#router ospf 26 DMVPN-Hub2(config-router)#router-id 10.1.5.3 DMVPN-Hub2(config-router)#network 10.1.5.0 255.255.255.0 area 0 DMVPN-Hub2(config-router)#network 3.3.3.3 255.255.255.255 area 0 DMVPN-Hub2(config-router)# DMVPN-Hub1#sh ip ospf neigh Neighbor ID Pri State Dead Time Address Interface 10.1.16.254 1 FULL/DR 00:00:38 10.1.4.254 GigabitEthernet0/0 DMVPN-Hub1# DMVPN-Hub2#sh ip ospf neigh Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 1 FULL/DR 00:00:39 10.1.3.2 GigabitEthernet0/3 10.1.26.254 1 FULL/BDR 00:00:15 10.1.5.254 GigabitEthernet0/0 DMVPN-Hub2#Let's add the ISP-1 router to OSPF:
ISP-1(config)#router ospf 1
ISP-1(config-router)#network 10.1.16.0 255.255.255.0 area 0
ISP-1(config-router)#network 10.1.26.0 255.255.255.0 area 0
ISP-1(config-router)#router-id 10.1.16.1
ISP-1(config-router)#
ISP-1(config-router)#do sh ip ospf neigh
ISP-1(config-router)#
FO-ASA/C1(config)# router ospf 16
FO-ASA/C1(config-router)# network 10.1.16.0 255.255.255.0 area 0
FO-ASA/C2(config)# router ospf 26
FO-ASA/C2(config-router)# network 10.1.26.0 255.255.255.0 area 0
FO-ASA/C2(config-router)#
ISP-1(config-router)#do sh ip route ospf | b Gate
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
O E2 1.1.1.1 [110/20] via 10.1.26.254, 00:00:28, GigabitEthernet0/0.2
3.0.0.0/32 is subnetted, 1 subnets
O IA 3.3.3.3 [110/12] via 10.1.26.254, 00:00:28, GigabitEthernet0/0.2
4.0.0.0/32 is subnetted, 1 subnets
O 4.4.4.4 [110/12] via 10.1.16.254, 00:02:02, GigabitEthernet0/0.1
10.0.0.0/8 is variably subnetted, 10 subnets, 2 masks
O 10.1.2.0/24 [110/13] via 10.1.26.254, 00:00:28, GigabitEthernet0/0.2
O 10.1.3.0/24 [110/12] via 10.1.26.254, 00:00:28, GigabitEthernet0/0.2
O 10.1.4.0/24 [110/11] via 10.1.16.254, 00:02:02, GigabitEthernet0/0.1
O 10.1.5.0/24 [110/11] via 10.1.26.254, 00:00:28, GigabitEthernet0/0.2
80.0.0.0/32 is subnetted, 1 subnets
O 80.2.10.1 [110/13] via 10.1.26.254, 00:00:28, GigabitEthernet0/0.2
ISP-1(config-router)#
Connect ISP-1 to ISP-2:ISP-1(config-router)#network 10.1.7.0 255.255.255.0 area 0 ISP-1(config-router)# ISP-2(config)#router ospf 1 ISP-2(config-router)#router-id 10.1.7.2 ISP-2(config-router)#network 10.1.7.0 255.255.255.0 area 0 ISP-2(config-router)#ISP-1 won't peer with ISP-2 at the moment, as we have a firewall in the way. To get the two to form an OSPF adjacency, we need to permit the OSPF traffic from ISP-2 in, and from ISP-1 out. OSPF uses two multicast addresses; 224.0.0.5 (All routers), 224.0.0.6 (Designated Routers), and we also allow the protocol between the joining hosts, and we also allow ping between the two ISP routers:
Transparent(config)# access-list Out->In extended permit ospf host 10.1.7.2 host 224.0.0.5 Transparent(config)# access-list Out->In extended permit ospf host 10.1.7.2 host 224.0.0.6 Transparent(config)# access-list Out->In extended permit ospf host 10.1.7.2 host 10.1.7.1 Transparent(config)# access-list Out->In extended permit icmp host 10.1.7.2 host 10.1.7.1 Transparent(config)# Transparent(config)# access-list In->Out extended permit ospf host 10.1.7.1 host 224.0.0.5 Transparent(config)# access-list In->Out extended permit ospf host 10.1.7.1 host 224.0.0.6 Transparent(config)# access-list In->Out extended permit ospf host 10.1.7.1 host 10.1.7.2 Transparent(config)# access-list In->Out extended permit icmp host 10.1.7.1 host 10.1.7.2 Transparent(config)# Transparent(config)# access-group Out->In in interface Outside Transparent(config)# access-group In->Out in interface Inside ISP-1# *Jun 30: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.7.2 on GigabitEthernet0/1 from LOADING to FULL, Loading Done ISP-1# ISP-2# *Jun 30: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.16.1 on GigabitEthernet0/1 from LOADING to FULL, Loading Done ISP-2# ISP-2#ping 10.1.7.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.7.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/6/10 ms ISP-2#This is a bit restrictive, however. We should probably allow more through, but I am sure that the lab exam won't allow access lists permitting IP "any any". We will come back this later, for the moment let's finish off the OSPF configuration:
ISP-2(config)#router ospf 1 ISP-2(config-router)#network 10.1.8.0 255.255.255.0 area 0 ISP-2(config-router)#network 10.1.9.0 255.255.255.0 area 0 ISP-2(config-router)# DMVPN-Client(config)#router ospf 1 DMVPN-Client(config-router)#router-id 5.5.5.5 DMVPN-Client(config-router)#network 10.1.8.0 255.255.255.0 area 0 DMVPN-Client(config-router)#network 5.5.5.5 255.255.255.255 area 0 *Jun 30: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.7.2 on GigabitEthernet0/2 from LOADING to FULL, Loading Done DMVPN-Client(config-router)# EzVPN-Server(config)#router ospf 1 EzVPN-Server(config-router)#router-id 6.6.6.6 EzVPN-Server(config-router)#network 10.1.9.0 255.255.255.0 area 0 EzVPN-Server(config-router)#network 6.6.6.6 255.255.255.255 area 0 *Jun 30: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.7.2 on GigabitEthernet0/3 from LOADING to FULL, Loading Done EzVPN-Server(config-router)#Now have end-to-end visibility:
RTD-ASA# sh route ospf | b Gate Gateway of last resort is not set O 4.4.4.4 255.255.255.255 [110/34] via 10.1.2.2, 00:30:33, Outside O 5.5.5.5 255.255.255.255 [110/25] via 10.1.2.2, 00:02:05, Outside O 6.6.6.6 255.255.255.255 [110/25] via 10.1.2.2, 00:00:49, Outside O 10.1.3.0 255.255.255.0 [110/11] via 10.1.2.2, 06:16:09, Outside O 10.1.4.0 255.255.255.0 [110/33] via 10.1.2.2, 00:30:33, Outside O 10.1.5.0 255.255.255.0 [110/12] via 10.1.2.2, 06:15:15, Outside O 10.1.7.0 255.255.255.0 [110/23] via 10.1.2.2, 00:26:58, Outside O 10.1.8.0 255.255.255.0 [110/24] via 10.1.2.2, 00:03:22, Outside O 10.1.9.0 255.255.255.0 [110/24] via 10.1.2.2, 00:03:12, Outside O 10.1.16.0 255.255.255.0 [110/23] via 10.1.2.2, 00:30:33, Outside O 10.1.26.0 255.255.255.0 [110/22] via 10.1.2.2, 00:30:43, Outside O 80.2.10.1 255.255.255.255 [110/11] via 10.1.2.2, 06:16:09, Outside RTD-ASA#We do not have reachability, though, because the traffic is not allowed through the transparent firewall or the Multi-context firewalls.
How do we fix this then? Should we permit everything through the firewalls or use NAT? If we NAT the networks behind the multi-context firewalls, then we lose the ability to have incoming traffic, well, if we overload, or PAT we do. Let's look at it another way; what do we need to achieve?
Ideally, all of the loopbacks should have connectivity, so we can exempt these like we did when setting up the IPSec between RTD-ASA and DMVPN-Hub2. This is important as the DMVPN clients will be peering to these addresses, but we could make it a bit more interesting by NAT'ing these address to external addresses and achieve the same result that way.
OK, so here's the plan:
- 1.1.1.1/32 will exempt from NAT
- 3.3.3.3/32 and 4.4.4.4/32 will be NAT'd on a one-to-one basis, to 10.1.26.200 and 10.1.16.200 respectively.
- 10.1.1.0/24, 10.1.2.0/24, 10.1.3.0/24, 10.1.5.0/24 will be PAT'd to the 10.1.26.254 address
- 10.1.4.0/24 will be PAT'd to the 10.1.16.254 address
Not a bad plan. But there is still an issue. Because everything is in area 0 the routes that will be hidden behind the NATs will be visible, so they need to be advertised, but not passed beyond the border firewall. Do we create more areas, or deny the prefixes from being advertised? Having one area keeps things nice and simple, but the CCIE is not a simple exam, so let's try and think like a proctor (or whoever designs the labs), and go for what I think is the harder choice, make more areas (well, one more area) and prevent some of the prefixes being advertised. The easy option would be to run multiple protocols, but I want to reserve EIGRP for use within the VPNs, and will also (if ISP-1 to the DPMVPN-Client and EzVPN-Server are in area 1) need to use a different protocol down the topology (EzVPN-Server to ZBF) to avoid having a discontiguous area 0.
So, now we have a bit of patching to do; first by creating the NATs, then by switching the areas, taking care of the advertisements of the hidden prefixes, and some hardening, because let's not forget that this is a security exam, so OSPF should be secured and authenticated.
But let's save all this for another day, as it's a bit late, I am two whiskeys in, and need a break.
The next day...
It's bugging me that the FO-ASAs outside interface (eth0) points to the Transparent ASA's Inside interface, really the interfaces on the transparent ASA should be swapped over. OK, strictly speaking, it doesn't matter one iota, but it's bugging me, so let's take care of that first before moving on.
Transparent(config)# int gi 0/1 Transparent(config-if)# no nameif Outside Transparent(config-if)# int gi0/0 Transparent(config-if)# nameif Outside Transparent(config-if)# int gi0/1 Transparent(config-if)# nameif Inside INFO: Security level for "Inside" set to 100 by default. Transparent(config-if)# sh run int gi0/0 ! interface GigabitEthernet0/0 nameif Outside bridge-group 1 security-level 100 Transparent(config-if)# sh run int gi0/1 ! interface GigabitEthernet0/1 nameif Inside bridge-group 1 security-level 100 Transparent(config-if)# int gi0/0 Transparent(config-if)# security-level 0 Transparent(config-if)# ISP-2#ping 10.1.7.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.7.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 3/3/4 ms ISP-2# *Jul 1: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.16.1 on GigabitEthernet0/1 from LOADING to FULL, Loading Done ISP-2#ping 10.1.7.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.7.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 5/6/7 ms ISP-2#That's a bit tidier now. However, OSPF is having issues, to we need to amend the access-lists created earlier (and invert them):
Transparent# sh run | i access-list access-list Out->In extended permit ospf host 10.1.7.2 host 224.0.0.5 access-list Out->In extended permit ospf host 10.1.7.2 host 224.0.0.6 access-list Out->In extended permit icmp host 10.1.7.2 host 10.1.7.1 access-list Out->In extended permit ospf host 10.1.7.2 host 10.1.7.1 access-list In->Out extended permit ospf host 10.1.7.1 host 224.0.0.5 access-list In->Out extended permit ospf host 10.1.7.1 host 224.0.0.6 access-list In->Out extended permit icmp host 10.1.7.1 host 10.1.7.2 access-list In->Out extended permit ospf host 10.1.7.1 host 10.1.7.2 threat-detection statistics access-list Transparent# Transparent# Transparent# conf t Transparent(config)# no access-list Out->In extended permit ospf host 10.1.7.2 host 224.0.0.5 Transparent(config)# no access-list Out->In extended permit ospf host 10.1.7.2 host 224.0.0.6 Transparent(config)# no access-list Out->In extended permit icmp host 10.1.7.2 host 10.1.7.1 Transparent(config)# no access-list Out->In extended permit ospf host 10.1.7.2 host 10.1.7.1 Transparent(config)# access-list Out->In extended permit ospf host 10.1.7.1 host 224.0.0.5 Transparent(config)# access-list Out->In extended permit ospf host 10.1.7.1 host 224.0.0.6 Transparent(config)# access-list Out->In extended permit icmp host 10.1.7.1 host 10.1.7.2 Transparent(config)# access-list Out->In extended permit ospf host 10.1.7.1 host 10.1.7.2 Transparent(config)# Transparent(config)# no access-list In->Out extended permit ospf host 10.1.7.1 host 224.0.0.5 Transparent(config)# no access-list In->Out extended permit ospf host 10.1.7.1 host 224.0.0.6 Transparent(config)# no access-list In->Out extended permit icmp host 10.1.7.1 host 10.1.7.2 Transparent(config)# no access-list In->Out extended permit ospf host 10.1.7.1 host 10.1.7.2 Transparent(config)# access-list In->Out extended permit ospf host 10.1.7.2 host 224.0.0.5 Transparent(config)# access-list In->Out extended permit ospf host 10.1.7.2 host 224.0.0.6 Transparent(config)# access-list In->Out extended permit ospf host 10.1.7.2 host 10.1.7.1 Transparent(config)# access-list In->Out extended permit icmp host 10.1.7.2 host 10.1.7.1 Transparent(config)# Transparent(config)# access-group In->Out in interface Inside Transparent(config)# access-group Out->In in interface Outside Transparent(config)#OSPF is stable again, so let's start with the NAT translations. The first of which is to exempt 1.1.1.1/32 from NAT, but we need to start with the RTD-ASA firewall, I have added an access-list to permit pings to and from 1.1.1.1:
RTD-ASA# sh run | i access- access-list IPSec-VPN-Traffic extended permit ip host 1.1.1.1 host 3.3.3.3 access-list NONAT extended permit ip object No-Nat-Networks object No-Nat-Destination access-list Out->In extended permit icmp host 1.1.1.1 any access-list Out->In extended permit icmp any host 1.1.1.1 access-group Out->In in interface Inside access-group Out->In in interface Outside threat-detection statistics access-list dynamic-access-policy-record DfltAccessPolicy RTD-ASA# FO-ASA/C2# ping 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/10 ms FO-ASA/C2# We create two network objects and use the "range" options, and one for the 1.1.1.1 network: FO-ASA/C2(config)# object network DontNat1-1-1-1-Main FO-ASA/C2(config-network-object)# range 10.1.7.0 10.1.26.254 FO-ASA/C2(config-network-object)# exit FO-ASA/C2(config)# object network DontNat1-1-1-1-Loops FO-ASA/C2(config-network-object)# range 5.5.5.5 9.9.9.9 FO-ASA/C2(config-network-object)# exit FO-ASA/C2(config)# object network 1-1-1-1 FO-ASA/C2(config-network-object)# host 1.1.1.1 FO-ASA/C2(config-network-object)# exit Next we create two NAT rules: FO-ASA/C2(config)# nat (Inside,Outside) source static 1-1-1-1 1-1-1-1 destination static DontNat1-1-1-1-Main DontNat1-1-1-1-Main no-proxy-arp route-lookup FO-ASA/C2(config)# nat (Inside,Outside) source static 1-1-1-1 1-1-1-1 destination static DontNat1-1-1-1-Loops DontNat1-1-1-1-Loops no-proxy-arp route-lookup FO-ASA/C2(config)# We can use the same access-list as before: FO-ASA/C2(config)# access-list Out->In extended permit icmp host 1.1.1.1 any FO-ASA/C2(config)# access-list Out->In extended permit icmp any host 1.1.1.1 FO-ASA/C2(config)# FO-ASA/C2(config)# access-group Out->In in interface Outside FO-ASA/C2(config)# access-group Out->In in interface Inside FO-ASA/C2(config)# Packet-tracer passes, but we need to move over to the Transparent ASA: Transparent(config)# access-list Out->In extended permit icmp host 1.1.1.1 any Transparent(config)# access-list In->Out extended permit icmp any host 1.1.1.1 Transparent(config)# EzVPN-Server#ping 1.1.1.1 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds: Packet sent with a source address of 6.6.6.6 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 18/19/21 ms EzVPN-Server# Local-1#ping 6.6.6.6 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 6.6.6.6, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 22/24/30 ms Local-1#First requirement done! Next we need to NAT 3.3.3.3/32 and 4.4.4.4/32 will (to 10.1.26.200 and 10.1.16.200 respectively).
FO-ASA/C2(config)# object network 3-3-3-3
FO-ASA/C2(config-network-object)# host 3.3.3.3
FO-ASA/C2(config-network-object)# nat (inside,outside) static 10.1.26.200
FO-ASA/C2(config-network-object)# access-list Out->In extended permit icmp host 3.3.3.3 any
FO-ASA/C2(config)# access-list Out->In extended permit icmp any host 3.3.3.3
FO-ASA/C2(config)#
Packet-tracer gives a clean report, but the pings fail:
DMVPN-Hub2#ping 6.6.6.6 so lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 6.6.6.6, timeout is 2 seconds:
Packet sent with a source address of 3.3.3.3
.....
Success rate is 0 percent (0/5)
DMVPN-Hub2#
Let's add the rules to the transparent FW:
Transparent(config)#
Transparent(config)# access-list Out->In extended permit icmp host 10.1.26.200 any
Transparent(config)# access-list In->Out extended permit icmp any host 10.1.26.200
Transparent(config)#
DMVPN-Hub2#ping 6.6.6.6 so lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 6.6.6.6, timeout is 2 seconds:
Packet sent with a source address of 3.3.3.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 13/18/31 ms
DMVPN-Hub2#
We will switch contexts and set up 4.4.4.4.
FO-ASA/C2# copy run start
Source filename [running-config]?
Cryptochecksum: 967e5e08 6159c480 83720b84 caa04442
2943 bytes copied in 0.240 secs
FO-ASA/C2#
FO-ASA/C2# changeto con C1
FO-ASA/C1#
FO-ASA/C1# conf t
FO-ASA/C1(config)# object network 4-4-4-4
FO-ASA/C1(config-network-object)# host 4.4.4.4
FO-ASA/C1(config-network-object)# nat (inside,outside) static 10.1.16.200
FO-ASA/C1(config-network-object)#
FO-ASA/C1(config-network-object)# access-list Out->In extended permit icmp host 4.4.4.4 any
FO-ASA/C1(config)# access-list Out->In extended permit icmp any host 4.4.4.4
FO-ASA/C1(config)#
FO-ASA/C1(config)# access-group Out->In in interface Outside
FO-ASA/C1(config)# access-group Out->In in interface Inside
FO-ASA/C1(config)#
Transparent(config)# access-list Out->In extended permit icmp host 10.1.16.200 any
Transparent(config)# access-list In->Out extended permit icmp any host 10.1.16.200
Transparent(config)#
DMVPN-Hub1#sh ip route ospf | b Gate
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
O E2 1.1.1.1 [110/20] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
3.0.0.0/32 is subnetted, 1 subnets
O IA 3.3.3.3 [110/23] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
5.0.0.0/32 is subnetted, 1 subnets
O 5.5.5.5 [110/14] via 10.1.4.254, 00:52:13, GigabitEthernet0/0
6.0.0.0/32 is subnetted, 1 subnets
O 6.6.6.6 [110/14] via 10.1.4.254, 00:52:13, GigabitEthernet0/0
10.0.0.0/8 is variably subnetted, 10 subnets, 2 masks
O 10.1.2.0/24 [110/24] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
O 10.1.3.0/24 [110/23] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
O 10.1.5.0/24 [110/22] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
O 10.1.7.0/24 [110/12] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
O 10.1.8.0/24 [110/13] via 10.1.4.254, 00:52:13, GigabitEthernet0/0
O 10.1.9.0/24 [110/13] via 10.1.4.254, 00:52:13, GigabitEthernet0/0
O 10.1.16.0/24 [110/11] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
O 10.1.26.0/24 [110/12] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
80.0.0.0/32 is subnetted, 1 subnets
O 80.2.10.1 [110/24] via 10.1.4.254, 04:23:28, GigabitEthernet0/0
DMVPN-Hub1#
DMVPN-Hub1#
DMVPN-Hub1#ping 6.6.6.6 so lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 6.6.6.6, timeout is 2 seconds:
Packet sent with a source address of 4.4.4.4
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 15/20/35 ms
DMVPN-Hub1#
EzVPN-Server#ping 10.1.16.200
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.16.200, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 15/20/27 ms
EzVPN-Server#ping 10.1.26.200
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.26.200, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 11/15/19 ms
EzVPN-Server#
FO-ASA/C1# sh xlate
1 in use, 1 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from Inside:4.4.4.4 to outside:10.1.16.200
flags s idle 0:00:11 timeout 0:00:00
FO-ASA/C1# copy run start
Source filename [running-config]?
Cryptochecksum: 27fd4949 bbe0dd79 a6dc5fac b7d2d457
2369 bytes copied in 0.240 secs
FO-ASA/C1#
So far, so good. Next up: 10.1.1.0/24, 10.1.2.0/24, 10.1.3.0/24, 10.1.5.0/24 will be PAT'd to the 10.1.26.254 address.Annoyingly I can't really use the range command to cover all of the subnets, as the 10.1.4.0/24 network belongs to a different context, so let's see what we can do instead. Object-groups would be a good thing here (note the change in context):
FO-ASA/C2(config)# object-group network GlobalNats FO-ASA/C2(config-network-object-group)# network-object 10.1.1.0 255.255.255.0 FO-ASA/C2(config-network-object-group)# network-object 10.1.2.0 255.255.255.0 FO-ASA/C2(config-network-object-group)# network-object 10.1.3.0 255.255.255.0 FO-ASA/C2(config-network-object-group)# network-object 10.1.5.0 255.255.255.0 FO-ASA/C2(config-network-object-group)# exit FO-ASA/C2(config)# sh object-g object-group network GlobalNats network-object 10.1.1.0 255.255.255.0 network-object 10.1.2.0 255.255.255.0 network-object 10.1.3.0 255.255.255.0 network-object 10.1.5.0 255.255.255.0 FO-ASA/C2(config)# FO-ASA/C2(config)# nat (inside,outside) source dynamic GlobalNats interface FO-ASA/C2(config)# Let's test with Packet tracer (the output has been truncated) after adding the ACL: FO-ASA/C2(config)# access-list Out->In extended permit icmp object-group GlobalNats any FO-ASA/C2(config)# access-list Out->In extended permit icmp any object-group GlobalNats FO-ASA/C2(config)# packet-tracer input inside icmp 10.1.2.254 8 0 6.6.6.6 Phase: 1 Type: ROUTE-LOOKUP Result: ALLOW Phase: 2 Type: ACCESS-LIST Result: ALLOW Config: access-group Out->In in interface inside access-list Out->In extended permit icmp object-group GlobalNats any object-group network GlobalNats network-object 10.1.1.0 255.255.255.0 network-object 10.1.2.0 255.255.255.0 network-object 10.1.3.0 255.255.255.0 network-object 10.1.5.0 255.255.255.0 Additional Information: Phase: 3 Type: NAT Result: ALLOW Config: nat (inside,outside) source dynamic GlobalNats interface Additional Information: Dynamic translate 10.1.2.254/0 to 10.1.26.254/29629 FO-ASA/C2(config)# Transparent(config)# access-list Out->In extended permit icmp host 10.1.26.254 any Transparent(config)# access-list In->Out extended permit icmp any host 10.1.26.254 Transparent(config)# CA-Flex#ping 6.6.6.6 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 6.6.6.6, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/19/30 ms CA-Flex#Now for the other context:
FO-ASA/C2# changeto con C1
FO-ASA/C1#
FO-ASA/C1# conf t
FO-ASA/C1(config)# object network GlobalNats
FO-ASA/C1(config-network-object)# subnet 10.1.4.0 255.255.255.0
FO-ASA/C1(config-network-object)# exit
FO-ASA/C1(config)# nat (inside,outside) source dynamic GlobalNats interface
FO-ASA/C1(config)# access-list Out->In extended permit icmp object GlobalNats any
FO-ASA/C1(config)# access-list Out->In extended permit icmp any object GlobalNats
FO-ASA/C1(config)#
Transparent(config)# access-list Out->In extended permit icmp host 10.1.16.254 any
Transparent(config)# access-list In->Out extended permit icmp any host 10.1.16.254
Transparent(config)#
DMVPN-Hub1#ping 6.6.6.6
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 6.6.6.6, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 18/21/27 ms
DMVPN-Hub1#
FO-ASA/C1(config)# sh xlate
3 in use, 3 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
NAT from Inside:4.4.4.4 to outside:10.1.16.200
flags s idle 0:00:17 timeout 0:00:00
NAT from outside:0.0.0.0/0 to Inside:0.0.0.0/0
flags sIT idle 0:00:03 timeout 0:00:00
ICMP PAT from Inside:10.1.4.4/3 to outside:10.1.16.254/3 flags ri idle 0:00:03 timeout 0:00:30
FO-ASA/C1(config)#
Nice! That is all the NATs set up. I kind of like having the transparent firewall in the way, it adds another level to the network, and is helping me think about the traffic flow, and what could potentially be blocking the traffic. The final thing to do is secure OSPF.Securing OSPF
At the moment we have hidden several networks behind NAT, but they are still visible in the control plane of the other routers:EzVPN-Server#sh ip route ospf | b Gate
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
O E2 1.1.1.1 [110/20] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
3.0.0.0/32 is subnetted, 1 subnets
O IA 3.3.3.3 [110/14] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
4.0.0.0/32 is subnetted, 1 subnets
O 4.4.4.4 [110/14] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
5.0.0.0/32 is subnetted, 1 subnets
O 5.5.5.5 [110/3] via 10.1.9.2, 14:47:50, GigabitEthernet0/3
10.0.0.0/8 is variably subnetted, 12 subnets, 2 masks
O 10.1.2.0/24 [110/15] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
O 10.1.3.0/24 [110/14] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
O 10.1.4.0/24 [110/13] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
O 10.1.5.0/24 [110/13] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
O 10.1.7.0/24 [110/2] via 10.1.9.2, 01:37:18, GigabitEthernet0/3
O 10.1.8.0/24 [110/2] via 10.1.9.2, 14:47:50, GigabitEthernet0/3
O 10.1.16.0/24 [110/3] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
O 10.1.26.0/24 [110/3] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
80.0.0.0/32 is subnetted, 1 subnets
O 80.2.10.1 [110/15] via 10.1.9.2, 01:29:48, GigabitEthernet0/3
EzVPN-Server#
We need to reconfigure OSPF into area 0, and area 1, hiding the NATd subnets from going between the areas. So, let's set up the areas, and hide the NATd subnets:
FO-ASA/C1(config)# sh run router ! router ospf 16 router-id 10.1.16.254 network 10.1.4.0 255.255.255.0 area 0 network 10.1.16.0 255.255.255.0 area 0 log-adj-changes ! FO-ASA/C1(config)# router ospf 16 FO-ASA/C1(config-router)# no network 10.1.16.0 255.255.255.0 area 0 FO-ASA/C1(config-router)# network 10.1.16.0 255.255.255.0 area 1 FO-ASA/C1(config-router)# ISP-1(config)#router ospf 1 ISP-1(config-router)#network 10.1.16.0 0.0.0.255 area 1 ISP-1(config-router)#network 10.1.7.0 0.0.0.255 area 1 ISP-1(config-router)#network 10.1.26.0 0.0.0.255 area 1 ISP-1(config-router)# FO-ASA/C1(config-router)# changeto con C2 FO-ASA/C2(config)# FO-ASA/C2(config)# sh run router ! router ospf 26 router-id 10.1.26.254 network 10.1.5.0 255.255.255.0 area 0 network 10.1.26.0 255.255.255.0 area 0 log-adj-changes ! FO-ASA/C2(config)# router ospf 26 FO-ASA/C2(config-router)# network 10.1.26.0 255.255.255.0 area 1 FO-ASA/C2(config-router)# ISP-2(config)#router ospf 1 ISP-2(config-router)#network 10.1.7.0 0.0.0.255 area 1 ISP-2(config-router)# *Jul 1: %OSPF-6-AREACHG: 10.1.7.0/24 changed from area 0 to area 1 *Jul 1: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.16.1 on GigabitEthernet0/1 from LOADING to FULL, Loading Done ISP-2(config-router)#network 10.1.8.0 0.0.0.255 area 1 *Jul 1: %OSPF-6-AREACHG: 10.1.8.0/24 changed from area 0 to area 1 ISP-2(config-router)# ISP-2(config-router)#network 10.1.9.0 0.0.0.255 area 1 *Jul 1: %OSPF-6-AREACHG: 10.1.9.0/24 changed from area 0 to area 1 ISP-2(config-router)# EzVPN-Server(config)#router ospf 1 EzVPN-Server(config-router)#network 6.6.6.6 0.0.0.0 area 1 EzVPN-Server(config-router)# *Jul 1: %OSPF-6-AREACHG: 6.6.6.6/32 changed from area 0 to area 1 EzVPN-Server(config-router)# EzVPN-Server(config-router)#network 10.1.9.0 0.0.0.255 area 1 EzVPN-Server(config-router)# *Jul 1: %OSPF-6-AREACHG: 10.1.9.0/24 changed from area 0 to area 1 *Jul 1: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.7.2 on GigabitEthernet0/3 from LOADING to FULL, Loading Done EzVPN-Server(config-router)# DMVPN-Client(config)#router ospf 1 DMVPN-Client(config-router)#network 5.5.5.5 0.0.0.0 area 1 DMVPN-Client(config-router)# *Jul 1: %OSPF-6-AREACHG: 5.5.5.5/32 changed from area 0 to area 1 DMVPN-Client(config-router)# DMVPN-Client(config-router)#network 10.1.8.0 0.0.0.255 area 1 DMVPN-Client(config-router)# *Jul 1: 10.1.8.0/24 changed from area 0 to area 1 DMVPN-Client(config-router)# DMVPN-Client(config-router)# *Jul 1: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.7.2 on GigabitEthernet0/2 from LOADING to FULL, Loading Done DMVPN-Client(config-router)# DMVPN-Client(config-router)#Now we can hide the NATd subnets:
FO-ASA(config)# changeto con C1
FO-ASA/C1(config)# router ospf 16
FO-ASA/C1(config-router)# area 0 range 10.1.4.0 255.255.255.0 not-advertise
FO-ASA/C1(config-router)# changeto con C2
FO-ASA/C2(config)# router ospf 26
FO-ASA/C2(config-router)# area 0 range 10.1.1.0 255.255.255.0 not-advertise
FO-ASA/C2(config-router)# area 0 range 10.1.2.0 255.255.255.0 not-advertise
FO-ASA/C2(config-router)# area 0 range 10.1.3.0 255.255.255.0 not-advertise
FO-ASA/C2(config-router)# area 0 range 10.1.5.0 255.255.255.0 not-advertise
FO-ASA/C2(config-router)#
EzVPN-Server#sh ip route ospf | b Gate
Gateway of last resort is not set
1.0.0.0/32 is subnetted, 1 subnets
O E2 1.1.1.1 [110/20] via 10.1.9.2, 00:03:18, GigabitEthernet0/3
4.0.0.0/32 is subnetted, 1 subnets
O IA 4.4.4.4 [110/14] via 10.1.9.2, 00:03:18, GigabitEthernet0/3
5.0.0.0/32 is subnetted, 1 subnets
O 5.5.5.5 [110/3] via 10.1.9.2, 00:17:31, GigabitEthernet0/3
10.0.0.0/8 is variably subnetted, 8 subnets, 2 masks
O 10.1.7.0/24 [110/2] via 10.1.9.2, 00:03:38, GigabitEthernet0/3
O 10.1.8.0/24 [110/2] via 10.1.9.2, 00:19:06, GigabitEthernet0/3
O 10.1.16.0/24 [110/3] via 10.1.9.2, 00:03:18, GigabitEthernet0/3
O 10.1.26.0/24 [110/3] via 10.1.9.2, 00:03:28, GigabitEthernet0/3
80.0.0.0/32 is subnetted, 1 subnets
O IA 80.2.10.1 [110/15] via 10.1.9.2, 00:03:18, GigabitEthernet0/3
EzVPN-Server#
Perfect. The thing to remember here is that the area range command specifies the area we are coming from, not going to. So the command "area 1 range 10.1.2.0 255.255.255.0 not-advertise", for example, does not work. Now let's get OSPF authenticated and nice and secure!
RTD-ASA(config)# router ospf 1
RTD-ASA(config-router)# area 0 authentication message-digest
RTD-ASA(config-router)# int gi0/1
RTD-ASA(config-if)# ospf authentication message-digest
RTD-ASA(config-if)# ospf message-digest-key 1 md5 cisco
RTD-ASA(config-if)#
CA-Flex(config)#router ospf 1
CA-Flex(config-router)#area 0 authentication message-digest
CA-Flex(config)#int gi0/1
CA-Flex(config-if)#ip ospf authentication message-digest
CA-Flex(config-if)#ip ospf mess
CA-Flex(config-if)#ip ospf message-digest-key 1 md5 cisco
CA-Flex(config-if)#
Jul 1: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.2.254 on GigabitEthernet0/1 from LOADING to FULL, Loading Done
CA-Flex(config-if)#
CA-Flex(config-if)#int gi 0/3
CA-Flex(config-if)#ip ospf authentication message-digest
CA-Flex(config-if)#ip ospf message-digest-key 1 md5 cisco
CA-Flex(config-if)#
DMVPN-Hub2(config)#router ospf 1
DMVPN-Hub2(config-router)#area 0 authentication message-digest
DMVPN-Hub2(config-router)#int gi 0/3
DMVPN-Hub2(config-if)#ip ospf authentication message-digest
DMVPN-Hub2(config-if)#ip ospf message-digest-key 1 md5 cisco
DMVPN-Hub2(config-if)#
DMVPN-Hub2(config-if)#int gi0/0
DMVPN-Hub2(config-if)#ip ospf authentication message-digest
DMVPN-Hub2(config-if)#ip ospf message-digest-key 1 md5 cisco
RTD-ASA# sh ospf interface outside
Outside is up, line protocol is up
Internet Address 10.1.2.254 mask 255.255.255.0, Area 0
Process ID 1, Router ID 10.1.2.254, Network Type BROADCAST, Cost: 10
Transmit Delay is 1 sec, State DR, Priority 1
Designated Router (ID) 10.1.2.254, Interface address 10.1.2.254
Backup Designated router (ID) 2.2.2.2, Interface address 10.1.2.2
Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5
oob-resync timeout 40
Hello due in 0:00:08
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 1/1, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 0, maximum is 2
Last flood scan time is 0 msec, maximum is 0 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 2.2.2.2 (Backup Designated Router)
Suppress hello for 0 neighbor(s)
Message digest authentication enabled <=== This is what we are looking for!
Youngest key id is 1
RTD-ASA#
CA-Flex#sh ip ospf interface | i protocol|authentication
Loopback100 is up, line protocol is up
GigabitEthernet0/3 is up, line protocol is up
Cryptographic authentication enabled
GigabitEthernet0/1 is up, line protocol is up
Cryptographic authentication enabled
CA-Flex#
I won't bore you with just repeating the same commands, but I set up authentication across the OSPF network. It's the same set of commands, so no point putting the entire lot here.Ths now means we should be able to set up DMVPN in the next post.