I know I said in the last post that I was saving NX-OS (Titanium) for another day, well, today is that day!
Finding a suitable vmdk file to use was the hardest part.. but in the end I did. I copied it to the tmp directory and tried the usual:
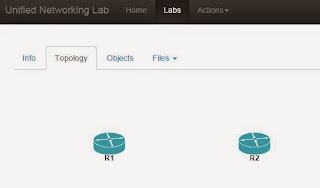
Topology:
From the documentation for CSR1000v it says to run:
However, this is not working for me:
This link would indicate that the module is not installed. I get the same when trying in VirtualBox. I did some googling and tried everything I can, turns out that my bargain ESXi box is missing one vital piece:
So I imported it into VMWare Fusion.
Now the message that the necessary bits arn't working has gone.
If you are having a similar issue then this is the screen that you don't want:
This is what you do want:
I can check that Qemu will be happy by doing this:
More importantly, the NX-OS routers fire up:
There we have it... NX-OS (Titanium) running inside of Unetlab. So if your virtualization platform supports a KVM guest, and you don't see "Warning: neither Intel VT-x or AMD-V found", then you should be OK.
Finding a suitable vmdk file to use was the hardest part.. but in the end I did. I copied it to the tmp directory and tried the usual:
root@iou:/tmp# ls N7K.vmdk root@iou:/tmp# qemu-img convert -f vmdk -O qcow2 N7K.vmdk hda.qcow2 root@iou:/tmp# mkdir /p /opt/unetlab/addons/qemu/titanium-7 root@iou:/tmp# mv hda.qcow2 /opt/unetlab/addons/qemu/titanium-7/ root@iou:/tmp# /opt/unetlab/wrappers/unl_wrapper -a fixpermissions root@iou:/tmp# ls -l /opt/unetlab/addons/qemu/ total 16 drwxr-xr-x 2 root root 4096 Feb 19 14:26 asa-8.42 drwxr-xr-x 2 root root 4096 Feb 19 16:16 titanium-7 drwxr-xr-x 2 root root 4096 Feb 19 13:53 vios-adventerprisek9-m15.4-1.2.0-173 drwxr-xr-x 2 root root 4096 Feb 17 11:02 xrv-k9-5.2.2 root@iou:/tmp#We have the files loaded and they are visible in Unetlab:
Topology:
Do they run?
Nope. They refuse to start.
From the documentation for CSR1000v it says to run:
# /usr/bin/qemu-system-x86_64 --enable-kvm -serial mon:stdio -nographic -boot order=c,once=d -smp 1 -m 3072 -usb -hda hda.qcow2 -cdrom csr1000v-universalk9.03.13.00.S.154-3.S-ext.iso
However, this is not working for me:
root@iou:/opt/unetlab/addons/qemu/titanium-7# /usr/bin/qemu-system-x86_64 --enable-kvm -serial mon:stdio -nographic -boot order=c,once=d -smp 1 -m 3072 -usb -hda hda.qcow2 -cdrom nexus.iso Could not access KVM kernel module: No such file or directory failed to initialize KVM: No such file or directory root@iou:/opt/unetlab/addons/qemu/titanium-7#
This link would indicate that the module is not installed. I get the same when trying in VirtualBox. I did some googling and tried everything I can, turns out that my bargain ESXi box is missing one vital piece:
So I imported it into VMWare Fusion.
Now the message that the necessary bits arn't working has gone.
If you are having a similar issue then this is the screen that you don't want:
This is what you do want:
I can check that Qemu will be happy by doing this:
More importantly, the NX-OS routers fire up:
We have connectivity...
NXOS1# sh ver
Cisco Nexus Operating System (NX-OS) Software
TAC support: http://www.cisco.com/tac
Documents: http://www.cisco.com/en/US/products/ps9372/tsd_products_support_serie
s_home.html
Copyright (c) 2002-2014, Cisco Systems, Inc. All rights reserved.
The copyrights to certain works contained herein are owned by
other third parties and are used and distributed under license.
Some parts of this software are covered under the GNU Public
License. A copy of the license is available at
http://www.gnu.org/licenses/gpl.html.
Titanium is a demo version of the Nexus Operating System
Software
loader: version N/A
kickstart: version 7.0(1) [build 7.0(1)ZD(0.216)]
system: version 7.0(1) [build 7.0(1)ZD(0.216)]
kickstart image file is: bootflash:///titanium-d1-kickstart.7.0.1.ZD.0.216.bin
kickstart compile time: 6/13/2014 20:00:00 [06/14/2014 05:45:18]
system image file is: bootflash:///titanium-d1.7.0.1.ZD.0.216.bin
system compile time: 6/13/2014 20:00:00 [06/14/2014 09:32:30]
Hardware
cisco Nexus7000 C7018 (18 Slot) Chassis ("Unknown Module")
Unknown CPU with 2042092 kB of memory.
Processor Board ID TM00010000B
Device name: NXOS1
bootflash: 0 kB
Kernel uptime is 0 day(s), 1 hour(s), 7 minute(s), 29 second(s)
plugin
Core Plugin, Ethernet Plugin
NXOS1#
NXOS1# sh cdp neigh
Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge
S - Switch, H - Host, I - IGMP, r - Repeater,
V - VoIP-Phone, D - Remotely-Managed-Device,
s - Supports-STP-Dispute
Device-ID Local Intrfce Hldtme Capability Platform Port ID
NXOS2(TB00020000B)
Eth2/1 141 R S s N7K-C7018 Eth2/1
NXOS1#
NXOS2# sh cdp neigh
Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge
S - Switch, H - Host, I - IGMP, r - Repeater,
V - VoIP-Phone, D - Remotely-Managed-Device,
s - Supports-STP-Dispute
Device-ID Local Intrfce Hldtme Capability Platform Port ID
NXOS1(TB00010000B)
Eth2/1 175 R S s N7K-C7018 Eth2/1
NXOS2#
There we have it... NX-OS (Titanium) running inside of Unetlab. So if your virtualization platform supports a KVM guest, and you don't see "Warning: neither Intel VT-x or AMD-V found", then you should be OK.