I did not manage to get any studying done over the weekend, so need to make up for it, that said, it was a good weekend. The annual Thai/Prague barbecue, where some of my wife's friends come over, and we eat some good food, have some good conversation and drink.
And I certainly did drink. Being the suave and cool-cat kind of guy I decided that (at about 10pm) bed would be the best option for me. My wife found me asleep on the bathroom floor at about midnight, whereupon I muttered something about having to "do the chicken", and then she put me to bed.
Yup. Stay classy Stuart.
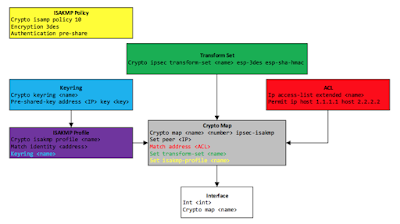
Anyway, I am picking up from last week and finishing off FlexVPN. To be honest I am having a hard time remembering all the required components of all the different VPNs, so created a VPNs Cheatsheet for each of the IOS VPNs. You can download it, I'll be doing more later on as well. It definitely came in handy today. But before we get to today, let's go back to last week - cue flashback wobbly screen and weird music...
Sometime last week...
Time to set up FlexVPN between Telnet-2 (Flex VPN client) and Telnet-1:
The configuration looks OK, and as the Flex VPN traffic will be carried within the IKE traffic, we do not need to worry about opening up the firewalls for the traffic between Telnet-1 and Telnet-2. However, the Flex VPN is not working. I can see the traffic, but nothing is getting established:
We'll need some debugging:
That's the hope anyway.
With not just over two months to go, things are starting to fall into place. I still need to memorize the VPN components, and build up the speed. But there is still plenty of time.
And I certainly did drink. Being the suave and cool-cat kind of guy I decided that (at about 10pm) bed would be the best option for me. My wife found me asleep on the bathroom floor at about midnight, whereupon I muttered something about having to "do the chicken", and then she put me to bed.
Yup. Stay classy Stuart.
Anyway, I am picking up from last week and finishing off FlexVPN. To be honest I am having a hard time remembering all the required components of all the different VPNs, so created a VPNs Cheatsheet for each of the IOS VPNs. You can download it, I'll be doing more later on as well. It definitely came in handy today. But before we get to today, let's go back to last week - cue flashback wobbly screen and weird music...
Sometime last week...
Time to set up FlexVPN between Telnet-2 (Flex VPN client) and Telnet-1:
Flex VPN Client configuration
Telnet-2(config)#crypto ikev2 client flexvpn FLEX-VPN Telnet-2(config-ikev2-flexvpn)#peer 1 1.1.1.1 Telnet-2(config-ikev2-flexvpn)#client connect tunnel 1 Telnet-2(config-ikev2-flexvpn)#exit Telnet-2(config)#int tunnel 1 Telnet-2(config-if)#tunnel destinatio 1.1.1.1 Telnet-2(config-if)#tun source loop 0 Telnet-2(config-if)#tunnel mode ipsec ipv4 Telnet-2(config-if)#tunnel protectio ipsec profile Flex-Protect Profile Flex-Protect is not defined. Telnet-2(config-if)# Telnet-2(config-if)#exit Telnet-2(config)#cryp ipsec profile Flex-Profile Telnet-2(ipsec-profile)#set transform-set 3des %ERROR: transform set with tag "3des" does not exist. Telnet-2(ipsec-profile)#exit Telnet-2(config)#cry ipsec transform-set 3des esp-3des esp-sha-hmac Telnet-2(cfg-crypto-trans)#exit Telnet-2(config)#cryp ipsec profile Flex-Profile Telnet-2(ipsec-profile)#set transform-set 3des Telnet-2(ipsec-profile)#int tunnel 1 Telnet-2(config-if)#tunnel protectio ipsec profile Flex-Profile Telnet-2(config-if)# %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON Telnet-2(config-if)#ip add nego Telnet-2(config-if)#do sh run | s crypto crypto ikev2 client flexvpn FLEX-VPN peer 1 1.1.1.1 crypto ipsec transform-set 3des esp-3des esp-sha-hmac mode tunnel crypto ipsec profile Flex-Profile set transform-set 3des Telnet-2(config-if)#exi Telnet-2(config)#aa new-model Telnet-2(config)#aaa authorization network AuthZ-list local Telnet-2(config)#crypto ikev2 proposal Flex-IKEv2-Prop IKEv2 proposal MUST either have a set of an encryption algorithm other than aes-gcm, an integrity algorithm and a DH group configured or encryption algorithm aes-gcm, a prf algorithm and a DH group configured Telnet-2(config-ikev2-proposal)#encryption 3des Telnet-2(config-ikev2-proposal)#integrity sha1 Telnet-2(config-ikev2-proposal)#group 5 Telnet-2(config-ikev2-proposal)#exit Telnet-2(config)#crypto ikev2 policy Flex-Policy IKEv2 policy MUST have atleast one complete proposal attached Telnet-2(config-ikev2-policy)#proposal Flex-IKEv2-Prop Telnet-2(config-ikev2-policy)#exit Telnet-2(config)#crypto ikev2 profile Flex-IKEv2-Prof IKEv2 profile MUST have: 1. A local and a remote authentication method. 2. A match identity or a match certificate or match any statement. Telnet-2(config-ikev2-profile)#authentication local pre-share Telnet-2(config-ikev2-profile)#auth remote pre-share Telnet-2(config-ikev2-profile)#$ity remote fqdn Telnet-1.ccielab.local Telnet-2(config-ikev2-profile)#identity local fqdn Telnet-2.ccielab.local Telnet-2(config-ikev2-profile)# Telnet-2(config-ikev2-profile)#keyring local Telnet1-Keyring % Invalid keyring Telnet1-Keyring Telnet-2(config-ikev2-profile)#exit Telnet-2(config)#cry ikev2 keyring Telnet1-Keyring Telnet-2(config-ikev2-keyring)#peer Telnet-1 Telnet-2(config-ikev2-keyring-peer)#address 1.1.1.1 Telnet-2(config-ikev2-keyring-peer)#pre-shared-key CCIE Telnet-2(config-ikev2-keyring-peer)#exit Telnet-2(config-ikev2-keyring)#exit Telnet-2(config)#crypto ikev2 profile Flex-IKEv2-Prof Telnet-2(config-ikev2-profile)#keyring local Telnet1-Keyring Telnet-2(config-ikev2-profile)# Telnet-2(config-ikev2-profile)#exit Telnet-2(config)#crypto ikev2 client flexvpn FLEX-VPN Telnet-2(config-ikev2-flexvpn)#client connect tunnel 1 Telnet-2(config-ikev2-flexvpn)# Telnet-2(config-ikev2-flexvpn)#exit Telnet-2(config)# Telnet-2(config)#do sh run | i profile crypto ikev2 profile Flex-IKEv2-Prof crypto ipsec profile Flex-Profile tunnel protection ipsec profile Flex-Profile Telnet-2(config)#crypto ipsec profile Flex-Profile Telnet-2(ipsec-profile)#set transform-set 3des Telnet-2(ipsec-profile)#set ikev2-profile Flex-IKEv2-Prof Telnet-2(ipsec-profile)#Hardly the smoothest setup in the work! Let's move on to the server:
Flex VPN Server configuration
Telnet-1(config)#ip local pool Flex-Pool 1.1.2.10 1.1.2.20 Telnet-1(config)# Telnet-1(config)#aaa new-model Telnet-1(config)# Telnet-1(config)#crypto ikev2 authorization policy default %Warning: This will Modify Default IKEv2 Authorization Policy. Exit if you don't want Telnet-1(config-ikev2-author-policy)#pool Flex-Pool Telnet-1(config-ikev2-author-policy)#exit Telnet-1(config)# Telnet-1(config)#cry ikev2 profile Flex-IKEv2-Policy IKEv2 profile MUST have: 1. A local and a remote authentication method. 2. A match identity or a match certificate or match any statement. Telnet-1(config-ikev2-profile)#authentication local pre-share Telnet-1(config-ikev2-profile)#auth remote pre Telnet-1(config-ikev2-profile)#$ity remote fqdn Telnet2.ccielab.local Telnet-1(config-ikev2-profile)#keyring local Flex-Keyring % Invalid keyring Flex-Keyring Telnet-1(config-ikev2-profile)#exi Telnet-1(config)#cry ikev2 keyring Flex-Keyring Telnet-1(config-ikev2-keyring)#peer Telnet1 Telnet-1(config-ikev2-keyring-peer)#address 2.2.2.2 Telnet-1(config-ikev2-keyring-peer)#pre CCIE Telnet-1(config-ikev2-keyring-peer)#exit Telnet-1(config-ikev2-keyring)#exit Telnet-1(config)#cry ikev2 profile Flex-IKEv2-Policy Telnet-1(config-ikev2-profile)#keyring local Flex-Keyring Telnet-1(config-ikev2-profile)#exit Telnet-1(config)# Telnet-1(config)#cry ikev2 proposal Flex-Prop IKEv2 proposal MUST either have a set of an encryption algorithm other than aes-gcm, an integrity algorithm and a DH group configured or encryption algorithm aes-gcm, a prf algorithm and a DH group configured Telnet-1(config-ikev2-proposal)#en 3des Telnet-1(config-ikev2-proposal)#int sha1 Telnet-1(config-ikev2-proposal)#gr 5 Telnet-1(config-ikev2-proposal)#exit Telnet-1(config)# Telnet-1(config)#cry ikev2 poli Telnet-1(config)#do sh run | i policy crypto ikev2 authorization policy default Telnet-1(config)#cry ikev2 policy Flex-Policy IKEv2 policy MUST have atleast one complete proposal attached Telnet-1(config-ikev2-policy)#proposal Flex-Prop Telnet-1(config-ikev2-policy)#exit Telnet-1(config)#cry ipsec profile Flex-IPSec-Prof Telnet-1(ipsec-profile)#set transform-set 3des %ERROR: transform set with tag "3des" does not exist. Telnet-1(ipsec-profile)#do sh run | i transf Telnet-1(ipsec-profile)#exit Telnet-1(config)#cry ips transform-set 3des esp-3des esp-sha-hmac Telnet-1(cfg-crypto-trans)#cry ipsec profile Flex-IPSec-Prof Telnet-1(ipsec-profile)#set transform-set 3des Telnet-1(ipsec-profile)#set ikev2-profile Flex-IKEv2-Policy Telnet-1(ipsec-profile)#exit Telnet-1(config)# Telnet-1(config)#int tun 1 Telnet-1(config-if)#ip unn loop0 Telnet-1(config-if)# Telnet-1(config-if)#tun so lo0 Telnet-1(config-if)#tun mo ipsec ipv4 Telnet-1(config-if)#tun prot ipsec prof Flex-IPSec-Prof Telnet-1(config-if)# Telnet-1(config-if)#cry ikev2 profile Flex-IKEv2-Policy Telnet-1(config-ikev2-profile)#virtual-template 1 Telnet-1(config-ikev2-profile)#exi Telnet-1(config)#int virtual-tem 1 t t Telnet-1(config-if)#ip unnu lo0 Telnet-1(config-if)#tun so lo0 Telnet-1(config-if)#tun mo ipse ipv4 Telnet-1(config-if)#tun prot ipsec profile Flex-IPSec-Prof Telnet-1(config-if)# %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON Telnet-1(config-if)# Telnet-1(config-if)#Present day:
The configuration looks OK, and as the Flex VPN traffic will be carried within the IKE traffic, we do not need to worry about opening up the firewalls for the traffic between Telnet-1 and Telnet-2. However, the Flex VPN is not working. I can see the traffic, but nothing is getting established:
We'll need some debugging:
Telnet-1#debug cry isak Crypto ISAKMP debugging is on Telnet-1#debug cry ikev2 clie Telnet-1#debug cry ikev2 client flex ISAKMP: (0):peer matches *none* of the profiles Telnet-1#debug cry ikev2 client flexvpn FlexVPN debugging is on Telnet-1# ISAKMP: (0):peer matches *none* of the profiles ISAKMP: (0):peer matches *none* of the profiles Telnet-1#We have the profiles set up, each should be identifying itself by the FQDN. Let's check:
Telnet-1#sh run | s crypto crypto ikev2 authorization policy default pool Flex-Pool no route set interface route set access-list Flex-Routes crypto ikev2 proposal Flex-Prop encryption 3des integrity sha1 group 5 crypto ikev2 policy Flex-Policy proposal Flex-Prop crypto ikev2 keyring Flex-Keyring peer Telnet1 address 2.2.2.2 pre-shared-key CCIE ! crypto ikev2 profile Flex-IKEv2-Policy match identity remote fqdn Telnet2.ccielab.local authentication remote pre-share authentication local pre-share keyring local Flex-Keyring aaa authorization group psk list AuthC default virtual-template 1 crypto ipsec transform-set 3des esp-3des esp-sha-hmac mode tunnel crypto ipsec profile Flex-IPSec-Prof set transform-set 3des set ikev2-profile Flex-IKEv2-Policy Telnet-1#We are expecting an FQDN of Telnet2.ccielab.local, but are actually being sent Telnet-2.ccielab.local. Let's fix it:
Telnet-2(config)#crypto ikev2 profile Flex-IKEv2-Prof Telnet-2(config-ikev2-profile)#no identity local fqdn Telnet-2.ccielab.local Telnet-2(config-ikev2-profile)#identity local fqdn Telnet2.ccielab.local Telnet-2(config-ikev2-profile)# Telnet-1(config)# ISAKMP: (0):peer matches Flex-IKEv2-Policy profile %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to up Telnet-1(config)#Now we can start to see some action, but what is true for one is true for the other, and the line flaps. I actually missed the local identity command from Telnet-1, I'd better add it:
Telnet-1(config)#crypto ikev2 profile Flex-IKEv2-Policy Telnet-1(config-ikev2-profile)#identity local fqdn Telnet-1.ccielab.local Telnet-1(config-ikev2-profile)# ISAKMP: (0):peer matches Flex-IKEv2-Policy profile %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to down %LINK-3-UPDOWN: Interface Virtual-Access2, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up Telnet-1(config-ikev2-profile)#do un all All possible debugging has been turned off Telnet-1(config-ikev2-profile)# Telnet-2(config-ikev2-profile)# %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel1, changed state to up Telnet-2(config-ikev2-profile)#do sh ip int bri Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0 10.1.13.1 YES NVRAM up up GigabitEthernet0/1 unassigned YES NVRAM administratively down down GigabitEthernet0/2 unassigned YES NVRAM administratively down down GigabitEthernet0/3 unassigned YES NVRAM administratively down down Loopback0 2.2.2.2 YES NVRAM up up Tunnel1 1.1.2.12 YES manual up up Telnet-2(config-ikev2-profile)#We now have a working tunnel, and the mistake I made was a very simple one. Still, hopefully the cheatsheet should help. I think its better to have the visual of how the different parts make up the VPNs, then just trying to blindly remember it!
That's the hope anyway.
With not just over two months to go, things are starting to fall into place. I still need to memorize the VPN components, and build up the speed. But there is still plenty of time.