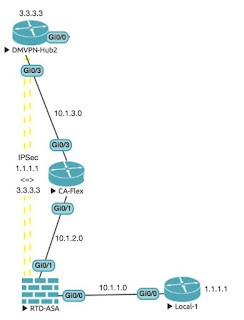
In the previous post, I switched the IKEv1 tunnel to a PKI-based IKEv2 tunnel. I got the desired result in the end but spent too much time searching for the answer, and in the lab exam there won't be any access to Google, so I need to be able to get it working first time around.
In this post, I will try and break down some of the reasons it did not work and set it up from scratch. I will be keeping the existing IP configuration, along with the NTP config, but the VPN will be set up again from scratch.
There is actually a useful command on the ASA, allowing you to migrate IKEv1 to IKEv2; it's the "migrate" command. However, this is not available on the IOS and despite the similarities between the two, when it comes to IKEv2 the command set does have some big differences.
Let's start by having a look at some of the issues and "gotchas".
Certificate lookup based on the HTTP URL avoids the fragmentation that results when large certificates are transferred. This feature is enabled on Cisco IOS software devices by default, so the cert req type 12 is used by Cisco IOS software.
If software versions that do not have the fix for Cisco bug ID CSCul48246 are used on the ASA, then the HTTP-URL-based lookup is not negotiated on the ASA, and Cisco IOS software causes the authorization attempt to fail.
On the ASA, if IKEv2 protocol debugs are enabled, these messages appear:
During IKE AUTH stage Internet Security Association and Key Management Protocol (ISAKMP) negotiations, the peers must identify themselves to each other. However, there is a difference in the way routers and ASAs select their local identity.
Therefore, we need to specify how the ASA presents itself to the IOS router, and vice-versa:
By default, the router uses the address as the local identity.
By contrast:
By default, the command mode is set to auto, which means that the ASA determines ISAKMP negotiation by connection type:
IP address for pre-shared key.
Cert Distinguished Name for certificate authentication.
This means that we need to specify how the router and the ASA present themselves. Which can be done as follows:
On the ASA tunnel is the setting "peer-id-validate nocheck" which circumvents some of the issues, and this is, in part, because I chose not to include the IP address when creating the certificate:
Similarly, by default the ASA selects the local ID automatically so, when cert auth is used, it sends the Distinguished Name (DN) as the identity. If the router is configured to receive the address as the remote ID, the peer ID validation fails on the router. For this issue, either configure the router in order to validate the fully qualified domain name (FQDN) or configure the ASA in order to use address as the ISAKMP ID.
What seems to have been the final "fix" was to create the certificate map on the router. Again the document linked above does clarify this approach:
On the router, a certificate map that is attached to the IKEv2 profile must be configured in order to recognize the DN.
This was done with the following:
I ran through this a couple of times. There was much cursing, googling and frustration, but I got it in the end.
Clearly, before the exam, I will need to run through it a couple of times again so that it is firmly ingrained.
Below are the steps for the ASA, followed by the IOS router. I have inserted comments, hopefully, to make it easier to read:
Next-up will dual-hub DMVPN!
In this post, I will try and break down some of the reasons it did not work and set it up from scratch. I will be keeping the existing IP configuration, along with the NTP config, but the VPN will be set up again from scratch.
There is actually a useful command on the ASA, allowing you to migrate IKEv1 to IKEv2; it's the "migrate" command. However, this is not available on the IOS and despite the similarities between the two, when it comes to IKEv2 the command set does have some big differences.
Let's start by having a look at some of the issues and "gotchas".
no crypto ikev2 http-url cert
This is a known issue, and pretty well documented:Certificate lookup based on the HTTP URL avoids the fragmentation that results when large certificates are transferred. This feature is enabled on Cisco IOS software devices by default, so the cert req type 12 is used by Cisco IOS software.
If software versions that do not have the fix for Cisco bug ID CSCul48246 are used on the ASA, then the HTTP-URL-based lookup is not negotiated on the ASA, and Cisco IOS software causes the authorization attempt to fail.
On the ASA, if IKEv2 protocol debugs are enabled, these messages appear:
IKEv2-PROTO-1: (139): Auth exchange failed IKEv2-PROTO-1: (140): Unsupported cert encoding found or Peer requested HTTP URL but never sent HTTP_LOOKUP_SUPPORTED NotificationIn order to avoid this issue, use the no crypto ikev2 http-url cert command in order to disable this feature on the router when it peers with an ASA.
IKEv2 Peer validation
The second issue I faced was the peer validation. Thankfully, this and the issue above, are documented in this link. I won't copy and paste the entire thing, but the nutshell is:During IKE AUTH stage Internet Security Association and Key Management Protocol (ISAKMP) negotiations, the peers must identify themselves to each other. However, there is a difference in the way routers and ASAs select their local identity.
Therefore, we need to specify how the ASA presents itself to the IOS router, and vice-versa:
By default, the router uses the address as the local identity.
By contrast:
By default, the command mode is set to auto, which means that the ASA determines ISAKMP negotiation by connection type:
IP address for pre-shared key.
Cert Distinguished Name for certificate authentication.
This means that we need to specify how the router and the ASA present themselves. Which can be done as follows:
Router: crypto ikev2 profile pro1 match identity remote fqdn RTD-ASA.ccielab.local identity local fqdn dmvpn-hub2.ccielab.local ASA: crypto isakmp identity hostnameUsing this setting on the ASA (with the domain-name set to ccielab.local) seems to have worked.
On the ASA tunnel is the setting "peer-id-validate nocheck" which circumvents some of the issues, and this is, in part, because I chose not to include the IP address when creating the certificate:
Similarly, by default the ASA selects the local ID automatically so, when cert auth is used, it sends the Distinguished Name (DN) as the identity. If the router is configured to receive the address as the remote ID, the peer ID validation fails on the router. For this issue, either configure the router in order to validate the fully qualified domain name (FQDN) or configure the ASA in order to use address as the ISAKMP ID.
What seems to have been the final "fix" was to create the certificate map on the router. Again the document linked above does clarify this approach:
On the router, a certificate map that is attached to the IKEv2 profile must be configured in order to recognize the DN.
This was done with the following:
crypto pki certificate map CA-Flex-Map 10 issuer-name co ca-flexI think the final issue was with the leftovers from the IKEv1 setup. Lots or reading as part of troubleshooting was done, but then I spent a lot of time thinking "Maybe I needed this bit, but not another bit". The "fvrf" command (front-door VRF) is an example of this. Clearly not enough time spent reading and learning before implementing. Now I will start again from scratch and this time document all the steps!
Cisco ASA to IOS IKEv2 with PKI
The steps are:- Create certificates
- Enroll in CA
- Create interesting traffic ACL
- Define crypto maps and proposals
- Create tunnels
I ran through this a couple of times. There was much cursing, googling and frustration, but I got it in the end.
Clearly, before the exam, I will need to run through it a couple of times again so that it is firmly ingrained.
Below are the steps for the ASA, followed by the IOS router. I have inserted comments, hopefully, to make it easier to read:
RTD-ASA(config)# crypto key generate rsa label RTD-ASA mod 1024 INFO: The name for the keys will be: RTD-ASA Keypair generation process begin. Please wait... ! ! Keys are generated - lets set up the CA trustpoint: ! RTD-ASA(config)# crypto ca trustpoint CA-Flex RTD-ASA(config-ca-trustpoint)# enrollment url http://80.2.10.1 RTD-ASA(config-ca-trustpoint)# crl configure RTD-ASA(config-ca-crl)# exit RTD-ASA(config-ca-trustpoint)# fqdn RTD-ASA.ccielab.local RTD-ASA(config-ca-trustpoint)# keypair RTD-ASA RTD-ASA(config-ca-trustpoint)# exit RTD-ASA(config)# RTD-ASA(config)# crypto ca authenticate CA-Flex INFO: Certificate has the following attributes: Fingerprint: 2a8252e6 eb4d9723 8f4e3480 1602cec3 Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted. RTD-ASA(config)# RTD-ASA(config)# crypto ca enroll CA-Flex % % Start certificate enrollment .. % Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it. Password: ******** Re-enter password: ******** % The fully-qualified domain name in the certificate will be: RTD-ASA.ccielab.local % Include the device serial number in the subject name? [yes/no]: no Request certificate from CA? [yes/no]: yes % Certificate request sent to Certificate Authority RTD-ASA(config)# RTD-ASA(config)# The certificate has been granted by CA! RTD-ASA(config)# ! ! Great, now let's define the interesting traffic and set up NAT ! RTD-ASA(config)# object network Nat-Networks RTD-ASA(config-network-object)# subnet 10.1.1.0 255.255.255.0 RTD-ASA(config-network-object)# object network No-Nat-Networks RTD-ASA(config-network-object)# host 1.1.1.1 RTD-ASA(config-network-object)# object network No-Nat-Destination RTD-ASA(config-network-object)# host 3.3.3.3 RTD-ASA(config-network-object)# access-list IPSec-VPN-Traffic extended permit ip host 1.1.1.1 host 3.3.3.3 RTD-ASA(config)# access-list NONAT extended permit ip object No-Nat-Networks object No-Nat-Destination RTD-ASA(config)# nat (Inside,Outside) source static No-Nat-Networks No-Nat-Networks destination static No-Nat-Destination No-Nat-Destination no-proxy-arp route-lookup ! ! Now we create the IKEv2 stuff, starting with the proposal ! RTD-ASA(config)# crypto ipsec ikev2 ipsec-proposal IKEv2-Proposal RTD-ASA(config-ipsec-proposal)# protocol esp encryption aes-256 3des RTD-ASA(config-ipsec-proposal)# protocol esp integrity sha-1 RTD-ASA(config-ipsec-proposal)# exit RTD-ASA(config)# ! ! Next come the policies - probably more than I actually need... ! RTD-ASA(config)# crypto ikev2 policy 10 RTD-ASA(config-ikev2-policy)# encryption 3des RTD-ASA(config-ikev2-policy)# integrity sha RTD-ASA(config-ikev2-policy)# group 5 RTD-ASA(config-ikev2-policy)# prf sha RTD-ASA(config-ikev2-policy)# exit RTD-ASA(config)# crypto ikev2 policy 20 RTD-ASA(config-ikev2-policy)# encryption aes-192 RTD-ASA(config-ikev2-policy)# integrity sha256 sha RTD-ASA(config-ikev2-policy)# group 14 5 2 RTD-ASA(config-ikev2-policy)# prf sha RTD-ASA(config-ikev2-policy)# lifetime seconds 86400 RTD-ASA(config-ikev2-policy)# exit RTD-ASA(config)# crypto ikev2 policy 30 RTD-ASA(config-ikev2-policy)# encryption 3des RTD-ASA(config-ikev2-policy)# integrity sha RTD-ASA(config-ikev2-policy)# group 5 2 RTD-ASA(config-ikev2-policy)# prf sha RTD-ASA(config-ikev2-policy)# lifetime seconds 86400 RTD-ASA(config-ikev2-policy)# exit RTD-ASA(config)# crypto ikev2 policy 40 RTD-ASA(config-ikev2-policy)# encryption aes-256 RTD-ASA(config-ikev2-policy)# integrity sha RTD-ASA(config-ikev2-policy)# group 14 5 2 RTD-ASA(config-ikev2-policy)# prf sha RTD-ASA(config-ikev2-policy)# lifetime seconds 86400 RTD-ASA(config-ikev2-policy)# exit ! ! We need to enable the Outside interface for IKEv2 ! RTD-ASA(config)# crypto ikev2 enable Outside ! ! Set the identity to be the hostname ! RTD-ASA(config)# crypto isakmp identity hostname RTD-ASA(config)# ! ! Now we create the tunnel, using a group policy to specify the protocol as IKEv2 ! RTD-ASA(config)# group-policy GroupPolicy2 internal RTD-ASA(config)# group-policy GroupPolicy2 attributes RTD-ASA(config-group-policy)# vpn-idle-timeout 30 RTD-ASA(config-group-policy)# vpn-tunnel-protocol ikev2 RTD-ASA(config-group-policy)# exit RTD-ASA(config)# tunnel-group 10.1.3.3 type ipsec-l2l RTD-ASA(config)# tunnel-group 10.1.3.3 general-attributes RTD-ASA(config-tunnel-general)# default-group-policy GroupPolicy2 RTD-ASA(config-tunnel-general)# exit ! ! This is where we tell the tunnel that we are sending a certificate, ! and expecting one in return. ! RTD-ASA(config)# tunnel-group 10.1.3.3 ipsec-attributes RTD-ASA(config-tunnel-ipsec)# ikev2 local-authentication certificate CA-Flex RTD-ASA(config-tunnel-ipsec)# ikev2 remote-authentication certificate RTD-ASA(config-tunnel-ipsec)# peer-id-validate nocheck RTD-ASA(config-tunnel-ipsec)# exit ! ! This is our crypto map: ! RTD-ASA(config)# crypto map VPN-Map 1 match address IPSec-VPN-Traffic RTD-ASA(config)# crypto map VPN-Map 1 set pfs group5 RTD-ASA(config)# crypto map VPN-Map 1 set peer 10.1.3.3 RTD-ASA(config)# crypto map VPN-Map 1 set ikev2 ipsec-proposal IKEv2-Proposal RTD-ASA(config)# crypto map VPN-Map 1 set reverse-route RTD-ASA(config)# crypto map VPN-Map interface Outside RTD-ASA(config)#Now the IOS router:
!
! Start by creating the crypto key
!
DMVPN-Hub2(config)#crypto key generate rsa mod 1024 label DMVPN-Hub2 exportable
The name for the keys will be: DMVPN-Hub2
% The key modulus size is 1024 bits
% Generating 1024 bit RSA keys, keys will be exportable...
[OK] (elapsed time was 1 seconds)
DMVPN-Hub2(config)#
Jun 30: %SSH-5-ENABLED: SSH 1.99 has been enabled
DMVPN-Hub2(config)#
!
! Next we set up the PKI trustpoint.
!
DMVPN-Hub2(config)#crypto pki trustpoint CA-Flex
DMVPN-Hub2(ca-trustpoint)#enrollment url http://80.2.10.1
DMVPN-Hub2(ca-trustpoint)#rsakeypair DMVPN-Hub2
DMVPN-Hub2(ca-trustpoint)#usage ike
DMVPN-Hub2(ca-trustpoint)#fqdn DMVPN-Hub2.ccielab.local
DMVPN-Hub2(ca-trustpoint)#revocation-check none
DMVPN-Hub2(ca-trustpoint)#eku request server-auth
DMVPN-Hub2(ca-trustpoint)#exit
DMVPN-Hub2(config)#
!
! Authenticate to the trustpoint
!
DMVPN-Hub2(config)#crypto pki authenticate CA-Flex
Certificate has the following attributes:
Fingerprint MD5: 2A8252E6 EB4D9723 8F4E3480 1602CEC3
Fingerprint SHA1: 0FB2B075 23BC42B6 54FEB918 0D384DD5 8AE6B8E1
% Do you accept this certificate? [yes/no]: yes
Trustpoint CA certificate accepted.
DMVPN-Hub2(config)#
!
! Enroll in the trustpoint
!
DMVPN-Hub2(config)#crypto pki enroll CA-Flex
%
% Start certificate enrollment ..
% Create a challenge password. You will need to verbally provide this
password to the CA Administrator in order to revoke your certificate.
For security reasons your password will not be saved in the configuration.
Please make a note of it.
Password:
Re-enter password:
% The subject name in the certificate will include: DMVPN-Hub2.ccielab.local
% Include the router serial number in the subject name? [yes/no]: no
% Include an IP address in the subject name? [no]: no
Request certificate from CA? [yes/no]: yes
% Certificate request sent to Certificate Authority
% The 'show crypto pki certificate verbose CA-Flex' commandwill show the fingerprint.
DMVPN-Hub2(config)#
Jun 30: CRYPTO_PKI: Certificate Request Fingerprint MD5: 67664772 0E859851 DFF2BA03 C9D727F4
Jun 30: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 13767DB5 F17DA7D6 CD3E2043 A968155D 77959542
Jun 30: %PKI-6-CERTRET: Certificate received from Certificate Authority
DMVPN-Hub2(config)#
!
! Define the interesting traffic
!
DMVPN-Hub2(config)#access-list 101 permit ip host 3.3.3.3 host 1.1.1.1
DMVPN-Hub2(config)#
!
! Create the IKEv2 proposal
!
DMVPN-Hub2(config)#crypto ikev2 proposal IKEv2-Proposal
IKEv2 proposal MUST either have a set of an encryption algorithm other than aes-gcm, an integrity algorithm and a DH group configured or
encryption algorithm aes-gcm, a prf algorithm and a DH group configured
DMVPN-Hub2(config-ikev2-proposal)#encryption aes-cbc-256
DMVPN-Hub2(config-ikev2-proposal)#integrity sha1
DMVPN-Hub2(config-ikev2-proposal)#group 5
DMVPN-Hub2(config-ikev2-proposal)#
DMVPN-Hub2(config-ikev2-proposal)#exit
DMVPN-Hub2(config)#
!
! Create a ikev2 policy
!
DMVPN-Hub2(config)#crypto ikev2 policy 10
IKEv2 policy MUST have atleast one complete proposal attached
DMVPN-Hub2(config-ikev2-policy)#match fvrf any
DMVPN-Hub2(config-ikev2-policy)#proposal IKEv2-Proposal
DMVPN-Hub2(config-ikev2-policy)#exit
DMVPN-Hub2(config)#
!
! Create a keyring
!
DMVPN-Hub2(config)#crypto ikev2 keyring ASA-Key
DMVPN-Hub2(config-ikev2-keyring)#peer RTD-ASA
DMVPN-Hub2(config-ikev2-keyring-peer)#address 10.1.2.254
DMVPN-Hub2(config-ikev2-keyring-peer)#exit
DMVPN-Hub2(config-ikev2-keyring)#
DMVPN-Hub2(config-ikev2-keyring)#exit
DMVPN-Hub2(config)#
!
! Create an IKEv2 profile
!
DMVPN-Hub2(config)#crypto ikev2 profile IKEv2-Profile
IKEv2 profile MUST have:
1. A local and a remote authentication method.
2. A match identity or a match certificate or match any statement.
DMVPN-Hub2(config-ikev2-profile)#match fvrf any
DMVPN-Hub2(config-ikev2-profile)#match identity remote address 10.1.2.254 255.255.255.255
DMVPN-Hub2(config-ikev2-profile)#match identity remote fqdn RTD-ASA.ccielab.local
DMVPN-Hub2(config-ikev2-profile)#match certificate CA-Flex-Map
%No such certificate map CA-Flex-Map
DMVPN-Hub2(config-ikev2-profile)#identity local dn
DMVPN-Hub2(config-ikev2-profile)#authentication local rsa-sig
DMVPN-Hub2(config-ikev2-profile)#authentication remote rsa-sig
DMVPN-Hub2(config-ikev2-profile)#keyring local ASA-Key
DMVPN-Hub2(config-ikev2-profile)#pki trustpoint CA-Flex
DMVPN-Hub2(config-ikev2-profile)#exit
DMVPN-Hub2(config)#
!
! Create the transform set
!
DMVPN-Hub2(config)#crypto ipsec transform-set IKEv2-Transform esp-3des esp-sha-hmac
DMVPN-Hub2(cfg-crypto-trans)#mode tunnel
DMVPN-Hub2(cfg-crypto-trans)#exit
DMVPN-Hub2(config)#
!
! Create the certificate map that should have been done before the profile...
!
DMVPN-Hub2(config)#crypto pki certificate map CA-Flex-Map 10
DMVPN-Hub2(ca-certificate-map)#issuer-name co CA-Flex
DMVPN-Hub2(ca-certificate-map)#exit
DMVPN-Hub2(config)#crypto ikev2 profile IKEv2-Profile
DMVPN-Hub2(config-ikev2-profile)#match certificate CA-Flex-Map
DMVPN-Hub2(config-ikev2-profile)#exit
DMVPN-Hub2(config)#
!
! Create the crypto map
!
DMVPN-Hub2(config)#crypto map VPN-Map 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
DMVPN-Hub2(config-crypto-map)#set peer 10.1.2.254
DMVPN-Hub2(config-crypto-map)#set transform-set IKEv2-Transform
DMVPN-Hub2(config-crypto-map)#set ikev2-profile IKEv2-Profile
DMVPN-Hub2(config-crypto-map)#match address 101
DMVPN-Hub2(config-crypto-map)#exit
!
! Enable the interface
!
DMVPN-Hub2(config)#int gi 0/3
DMVPN-Hub2(config-if)#crypto map VPN-Map
DMVPN-Hub2(config-if)#exit
Jun 30: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
DMVPN-Hub2(config)#
!
! Disable HTTP certificate lookups
!
DMVPN-Hub2(config)#no crypto ikev2 http-url cert
DMVPN-Hub2(config)#
There is a lot to remember here, and a lot to forget. I will need to run through this a couple of times! But the tunnel is up and working:Local-1#ping 3.3.3.3 so lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 6/9/11 ms
Local-1#
RTD-ASA# sh crypto ikev2 sa
IKEv2 SAs:
Session-id:2, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
46168045 10.1.2.254/500 10.1.3.3/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/21 sec
Child sa: local selector 1.1.1.1/0 - 1.1.1.1/65535
remote selector 3.3.3.3/0 - 3.3.3.3/65535
ESP spi in/out: 0x33701b89/0xacbd1af8
RTD-ASA#
DMVPN-Hub2#sh crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 10.1.3.3/500 10.1.2.254/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA1, Hash: SHA96, DH Grp:5, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/48 sec
IPv6 Crypto IKEv2 SA
DMVPN-Hub2#
This one will get revisited, most likely in the form of a break-fix scenario. But now it's time to move on (mainly because I am annoyed that this is taking a while to get into my head).Next-up will dual-hub DMVPN!