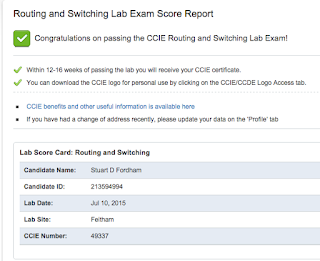
So, let me start by saying that I don't know my result yet, it's nearly 11pm on a Friday night. I have a thumping headache, and after getting only a couple of hours sleep last night, I am feeling very tired.
Let me also say that I won't be breaking any NDA in this post (or outside of the post, so don't ask for any lab details).
That said, here's how my day went.
I got very little sleep. My body has a tendency to wake me up super early if I have something important to do, today was no exception. My alarm was set for 7am, brain woke me up at 5am. Screw you brain. Thanks a bunch. Managed to get an hour or so sleep after that, woke up feeling very groggy.
The shower at the hotel was decent enough, so that woke me up a bit, I got a coffee from Starbucks, and drove over to the Cisco campus.
The campus is very nice. I didn't take any pictures, already the nerves had kicked in, and I turned my phone off and stored it in the car.
I arrived about half an hour early, one of three candidates, the other two were taking the DC track.
We sign some paper work, and head up to the room.
I have got the most wobbly desk. It's like typing on a boat. I also have one of those keyboards with a really small enter key, and a \ next to it. So very frequently I pressed \ instead of enter, which got really infuriating for a while, but seemed to get easier (a little) later on.
We only have putty, no SecureCrt, or superputty. This is a little annoying, but you get used to it. The screen is a decent size though.
First up we have the troubleshooting section. I am whizzing through this, the first seven questions go really well, and the last two went well also. I did have to ask the proctor at one stage, but he couldnt help me. Everything was working fine, so it's my issue. I did solve that one myself though, so that was OK. Question 8, however, I could not get to work. It kind of worked, but not 100%. So I reckon I failed on that one. The annoying thing is that the first bunch of questions I whizzed through. Got stumped on #8, did 9 and 10 then went back to 8. Still couldn't get the output to match, I had bags of time, and even went into the 30 mins that could be used for the Config section. Still couldn't get it to work.
At this point I got really angry and stressed at myself. Routes were there, just things were taking the wrong path. I spent ages going over and over it. Getting more and more stressed. In the end I decided to move on, and save the time for the config section.
As a side note - I know a lot of people have mentioned that there is a fair amount of lag in a remote lab, but I found it perfectly fine.
Then we have the Diagnostic, which I think went OK. Again, I havn't got the scores yet, so it might have gone ok, or I might have bombed out completely.
Its about 11:30 by now, so I start the config section, covering all of section 1 before lunch.
The cafeteria at Cisco is very nice, but I just opted for an orange juice. Nerves had hit hard by then. I was till angry over the question I had failed to solve in the TS, so was stewing a bit.
The config section went pretty well (I think, we'll find out at some stage). I didn't leave any questions un-attempted, and the outputs matched what was required.
I finished with about 2 minutes to spare. It was close, and I know I picked up a couple of points in the IPv6 section that I would have otherwise missed if I had not had those extra couple of minutes that I chose to "lose" from the TS section.
So although I know I lost some points in the TS, I gained some in the config.
I walked out feeing very uncertain. If I had got all of the TS tickets, then I am sure that I'd have a passing grade, as it stands now, I really don't know.
I then spent about 2 hours on the M25, before getting home and meeting my wife and kids at the family-do at the local cricket club.
Now it's 11:20pm. I am tired, a little drunk, and off to bed. Still none the wiser as to whether or not I have passed. Though the title of this post should be an indication of how well I think I did.
Before I go though, I'd like to say a big thank you to all of you who have wished me well for today, either through the blog, through twitter, or via any other means. It meant a lot, and thank you.
Night all.