I posted
yesterday about the IPS, in that it had a tendency to go to sleep on me, and not wake up. However, the IPS is a pretty big part of the CCIE Security lab, so it needs to be working! Through the power of the internet, it turns out that this is not an uncommon issue.
This guy is also working towards his CCIE Security, so follow him on Twitter.
So I started again from scratch, new source, followed the IPS creation docs (see the cznetlab link from yesterday), and everything booted up.
So I ran the setup:
sensor# setup
--- Basic Setup ---
--- System Configuration Dialog ---
At any point you may enter a question mark '?' for help.
User ctrl-c to abort configuration dialog at any prompt.
Default settings are in square brackets '[]'.
Current time: Wed May 4 09:45:54 2016
Setup Configuration last modified: Wed May 04 09:45:35 2016
Enter host name[sensor]: IPS-4240
Enter IP interface[192.168.1.2/24,192.168.1.1]: 10.1.4.155/24,10.1.4.254
Modify current access list?[no]: yes
Current access list entries:
No entries
Permit: 10.1.4.0/24
Permit: 10.1.20.0/24
Permit:
Use DNS server for Global Correlation?[no]:
Use HTTP proxy server for Global Correlation?[no]:
Modify system clock settings?[no]:
Participation in the SensorBase Network allows Cisco to
collect aggregated statistics about traffic sent to your IPS.
SensorBase Network Participation level?[off]:
The following configuration was entered.
service host
network-settings
host-ip 10.1.4.155/24,10.1.4.254
host-name IPS-4240
telnet-option disabled
access-list 10.1.4.0/24
access-list 10.1.20.0/24
ftp-timeout 300
no login-banner-text
dns-primary-server disabled
dns-secondary-server disabled
dns-tertiary-server disabled
http-proxy no-proxy
exit
time-zone-settings
offset 0
standard-time-zone-name UTC
exit
summertime-option disabled
ntp-option disabled
exit
service global-correlation
network-participation off
exit
[0] Go to the command prompt without saving this config.
[1] Return to setup without saving this config.
[2] Save this configuration and exit setup.
[3] Continue to Advanced setup.
Enter your selection[3]: 2
Warning: DNS or HTTP proxy is required for global correlation inspection and reputation filtering, but no DNS or proxy servers are defined.
--- Configuration Saved ---
Complete the advanced setup using CLI or IDM.
To use IDM,point your web browser at https://.
sensor#
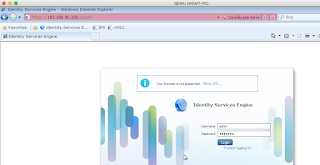
All looked good. I switched to non-TLS, and IDM started to load... then hung. Again the IPS won't communicate with anything else.
So I get another IPS-4240 source, and the same things happens again. This is really starting to piss me off now.
Oddly, it only seems to crap out once I start to use the GUI, so could this be the issue? Am I destined know IPS purely by the CLI? That's no bad thing. So let's see how far I can go in the CLI. Starting by creating some users. Thankfully the IPS supports context sensitive help, and there is a username command:
IPS-4240(config)# username ipsadmin privilege administrator password Admin1234
IPS-4240(config)# username ipsoper privilege operator password Oper1234
IPS-4240(config)# username ipsview privilege viewer password View1234
IPS-4240(config)#
That was a nice, easy start. The rest of the cool stuff lives under the "service command":
IPS-4240(config)# service ?
aaa Enter configuration mode for AAA options.
analysis-engine Enter configuration mode for global analysis engine options.
anomaly-detection Enter configuration mode for anomaly-detection.
authentication Enter configuration mode for user authentication options.
event-action-rules Enter configuration mode for the event action rules.
external-product-interface Enter configuration mode for the interfaces to external products.
global-correlation Enter configuration mode for global correlation configuration.
health-monitor Enter configuration mode for health and security monitoring.
host Enter configuration mode for host configuration.
interface Enter configuration mode for interface configuration.
logger Enter configuration mode for debug logger.
network-access Enter configuration mode for the network access controller.
notification Enter configuration mode for the notification application.
signature-definition Enter configuration mode for the signature definition.
ssh-known-hosts Enter configuration mode for configuring SSH known hosts.
trusted-certificates Enter configuration mode for configuring trusted certificates.
web-server Enter configuration mode for the web server application.
IPS-4240(config)# service
Let's try and create a new signature. This will have some basic goals. It'll produce a high-severity alert on matches to tcp port 93. I kind of stumbled my way through, so have cleaned it up a bit:
IPS-4240(config)# service signature-definition sig2
Editing new instance sig2.
IPS-4240(config-sig)#
IPS-4240(config-sig)# signatures ?
<1000-65000>
IPS-4240(config-sig)# signatures 65000 ?
<0-255>
IPS-4240(config-sig)# signatures 65000 0
IPS-4240(config-sig-sig)# alert-severity ?
high Dangerous Alert.
medium Medium level alert
low Low level alert
informational Informational alert.
IPS-4240(config-sig-sig)# alert-severity high
IPS-4240(config-sig-sig)# engine atomic-ip
IPS-4240(config-sig-sig-ato)# ?
default
event-action
exit
fragment-status
no
show
specify-ip-addr-options
specify-ip-header-length
specify-ip-id
specify-ip-option-inspection
specify-ip-payload-length
specify-ip-tos
specify-ip-total-length
specify-ip-ttl
specify-ip-version
specify-l4-protocol
swap-attacker-victim
IPS-4240(config-sig-sig-ato)# event-action produce-alert
IPS-4240(config-sig-sig-ato)# specify-l4-protocol yes
IPS-4240(config-sig-sig-ato-yes)# l4-protocol tcp
IPS-4240(config-sig-sig-ato-yes-tcp)# exit
Error: /tcp/tcp-flags/ -- the value is empty and has no default
/tcp/tcp-mask/ -- the value is empty and has no default
% Please answer 'yes' or 'no'. no]: no tcp-flags
Would you like to exit anyway?[no]: no
IPS-4240(config-sig-sig-ato-yes-tcp)# no tcp-flags
IPS-4240(config-sig-sig-ato-yes-tcp)# no tcp-mask
IPS-4240(config-sig-sig-ato-yes-tcp)# specify-dst-port yes
IPS-4240(config-sig-sig-ato-yes-tcp-yes)# dst-port 93
IPS-4240(config-sig-sig-ato-yes-tcp-yes)# exit
IPS-4240(config-sig-sig-ato-yes-tcp)# exit
IPS-4240(config-sig-sig-ato-yes)# exit
IPS-4240(config-sig-sig-ato)# exit
IPS-4240(config-sig-sig)# exit
Apply Changes?[yes]: yes
IPS-4240(config)#
So, that took a fair amount of time, so I thought I'd see if I could access it by the IDM, just in case I wasn't waiting long enough after booting. But even without trying IDM, I had still lost contact with the network:
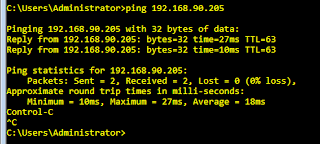
IPS-4240# ping 10.1.4.254
PING 10.1.4.254 (10.1.4.254): 56 data bytes
--- 10.1.4.254 ping statistics ---
4 packets transmitted, 0 packets received, 100% packet loss
IPS-4240#
Arse.
This is going to make using the IPS as an IPS so much harder!
Broadening the Google search I can across these posts:
https://supportforums.cisco.com/discussion/12207411/ips-70-gns3
https://gns3.com/qa/ips-7-network-connection-refused
Both have a similar issue (Connection Refused) - but that's through Telnet, whereas I would not see this on the console. The proposed fix is this though:
Qemu Options: -smbios type=1,product=IPS-4240,version=1.0,serial=12345789012,uuid=E0A32395-8DFE-D511-8C31-001FC641BA6B,sku=011,family=IPS-4240
The existing UNL template can be amended to achieve this quite easily.
So let's give this a go!
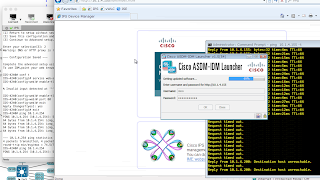
I edited the template, deleted and readded the IPS, fired it up, reconfigured it, and....
Yep. It all stops again.
So I rebooted. EVERYTHING. All nodes were stopped. I turned the oven on (not related, I'm just hungry), UNL got rebooted, I closed the lab and reopened it, and things were started again.
So, what do you reckon?
Did it work?
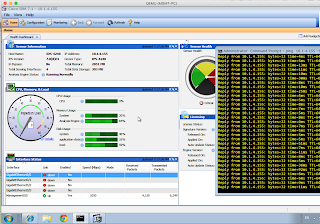
Actually, I think it might have done. IDM has loaded, and the ping seems solid:
So, for those having the same issue at home, just a little recap (some steps may not be needed, but this is what has worked for me tonight):
Turn off all nodes
Edit the template file: /opt/unetlab/html/templates/cips.php
Use this code:
<?php
# vim: syntax=php tabstop=4 softtabstop=0 noexpandtab laststatus=1 ruler
/**
* html/templates/cips.php
*
* cips template for UNetLab.
*
* LICENSE:
*
* This file is part of UNetLab (Unified Networking Lab).
*
* UNetLab is free software: you can redistribute it and/or modify
* it under the terms of the GNU General Public License as published by
* the Free Software Foundation, either version 3 of the License, or
* (at your option) any later version.
*
* UNetLab is distributed in the hope that it will be useful,
* but WITHOUT ANY WARRANTY; without even the implied warranty of
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.See the
* GNU General Public License for more details.
*
* You should have received a copy of the GNU General Public License
* along with UNetLab.If not, see .
*
* @author Andrea Dainese
* @copyright 2014-2016 Andrea Dainese
* @license http://www.gnu.org/licenses/gpl.html
* @link http://www.unetlab.com/
* @version 20151116
*/
$p['type'] = 'qemu';
$p['name'] = 'IPS';
$p['icon'] = 'Network Analyzer.png';
$p['cpu'] = 1;
$p['ram'] = 2048;
$p['ethernet'] = 5;
$p['console'] = 'telnet';
$p['qemu_arch'] = 'i386';
$p['qemu_version'] = '1.3.1';
$p['qemu_options'] = '-machine type=pc-1.0 -serial mon:stdio -nographic -nodefconfig -nodefaults -rtc base=utc -no-shutdown -boot order=c -smbios type=1,product=IPS-4240/4255,version=1.0,serial=12345789012,uuid=E0A32395-8DFE-D511-8C31-001FC641BA6B,sku=011,family=IPS-4240/4255';
?>
Save it
Reboot UNL (completely)
Start things up again.
Hopefully it will work for you as well!
This is the only time I have been able to get into IDM, and so far (all 12 minutes), it has been stable!
EDIT: Make that 17 minutes! Wooo Hooo!
 ) is a big weighty tome, of all the Cisco Security books on my desk, it's probably the biggest. I have started to read it, but did not get that far. So I tried watching the INE videos, which I thought would make getting back into the book a bit easier, but the sheer size of it puts me off.
) is a big weighty tome, of all the Cisco Security books on my desk, it's probably the biggest. I have started to read it, but did not get that far. So I tried watching the INE videos, which I thought would make getting back into the book a bit easier, but the sheer size of it puts me off.