There are some people around who, through the magic of modern technology (Twitter), put my studying efforts to shame. To name a couple we have @seawanderer, @darby_weaver, and @mzStanikzai. I see them working hard, and quite frankly it's putting my build up the CCIE Security lab to shame.
But, thanks to them, it's given me a newfound impetus to up my game. I won't be filling my study with racks of equipment, like Mr. Weaver (because the long-haired boss would do her nut), but certainly, it's given me a well-needed kick up the arse. Besides, I'd much rather be reading about ISE, than watching Sharkboy and Lavagirl. They say you are never fully prepared for fatherhood, but so far it's been a breeze compared to watching that monstrosity of a film. I can only imagine that the meetings for the film went something like this:
Meeting 1:
Executive: So, "Sharkboy and Lavagirl"? Were you smoking crack when you came up with this?
Writer: Yes
Executive: Pass me some. I'm going to need it if I am going to get this crap passed by finance.
Meeting 2:
Writer: We are 65% done, need to finish off the last 35%
Executive: Fill the rest with shitty puns, no one will notice.
Writer: I'll go do a shit-load more drugs and come up with something.
Meeting 3:
Executive: We only managed to finish 25% of it with puns, we still need something for the last 10%
Other executive: Let's make it 3D, no one will care that the rest of it sucks balls.
Executive (hitting crack pipe): I thought it was 3D already...
For all the benefits of Amazon prime, there are some downsides.
Anyway, it's game on and I will make ISE my bitch this week.
So, we need a game plan, otherwise it's just me bungling through it, hoping for best. This is what I have come up with so far:
1: Set up AD server (again, had password issues, so have rebuilt it)
2: Install certificate services - ISE will need these, and join to AD.
3: Set up the 3750X switch for Radius auth to ISE
4: Set up the WLC for Radius auth to ISE
5: Test it, tweak it
6: Drink.
Number 1 was easy enough, but number 2 provided some issues:
It's something about having the CA on the DC. But this can be got around by running the command "certreq -submit -attrib certificatetemplate:webserver" and browsing for ht PEM file created by the ISE.
Anyway, once that was all sorted, and I installed Firefox to get around some knock-on issues, I could move forward and connect the ISE node to AD. By "connect the ISE node to AD" I do of course mean google the myriad of errors that come up, and swear a lot. Some of this was my fault - I fat-fingered the domain name, and then had to sort out issues with NTP (clock skew). It's been a few hours and I still have not gotten very far. This would be far easier in a "proper" environment, there are just too many variables when working in an all-virtualized environment, using devices you have had to beg, borrow and steal. But there you go. Such is life. I am sure that when it is all working, it'll all be fine.
Someone tell me it'll all be fine... Or just to man-up and get on with it...
I think whilst ISE does it's umpteenth reboot it's time to go and finish off the rest of yesterdays home-made lasagna. When not being frustrated at the CCIE Security track, I am a pretty decent cook. Though I did make a Thai prawn red curry the other day that was a little too hot for my liking. The wife loved it, but then she spent three years in Thailand, so is used to having food that hot.
Before stepping off for some food, I thought I'd give it one last go, hoping that fixing the NTP server issue, things might magically work... and the did:
I do like a green tick box icon!
Now we are getting somewhere! But I really am off for some food now.
2 days later...
So the good news is that since getting the ISE AD-integrated, it has been much more stable. I have got flash loaded onto the Firefox, and the ISE looks good. I wouldn't say perfect, as something does look like it goes to sleep, I have to ping the local address on SW4 (192.168.90.4) before ISE can talk to the AD server (10.1.4.100). It could be an image issue, it could be UNetLab or ESXi saving resources... not sure, but I think I can live with it for the moment. The management PC has now been moved to the same VLAN, and that has no issue getting to the ISE. I have changed the default gateway on the ISE server to be the VIF on SW4, so maybe that will improve things.
So, let's start trying to get the switch to talk to ISE.
We begin by adding a Network Device Group and Location
Adding a location is pretty similar
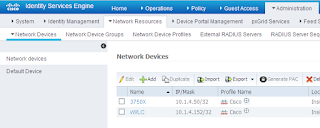
Next we can add the switch:
Setting the Shared Secret to Radius123:
Configuration-wise, we'll start with the old commands, and then see that thse are deprecated, and use the new format:
3750X(config)#aaa new-model 3750X(config)#line vty 0 4 3750X(config-line)#width 255 3750X(config-line)#exi 3750X(config)#radius-server host 192.168.90.205 auth-port 1812 acct-port 1813 key 0 Radius123 Warning: The CLI will be deprecated soon 'radius-server host 192.168.90.205 auth-port 1812 acct-port 1813 key 0 Radius123' Please move to 'radius serverThe next step is to direct our logins to the ISE. I have created an account in AD for myself to test with.' CLI. 3750X(config)# 3750X(config)#no radius-server host 192.168.90.205 auth-port 1812 acct-port 1813 key 0 Radius123 3750X(config)#radius server ISE20 3750X(config-radius-server)#address ipv4 192.168.90.205 auth-port 1812 acct-port 1813 3750X(config-radius-server)#key 0 Radius123 3750X(config-radius-server)#exit 3750X(config)#aaa group server radius ISE 3750X(config-sg-radius)#server name ISE20 3750X(config-sg-radius)#deadtime 15 3750X(config-sg-radius)#
3750X(config)#aaa authentication ? arap Set authentication lists for arap. attempts Set the maximum number of authentication attempts banner Message to use when starting login/authentication. dot1x Set authentication lists for IEEE 802.1x. enable Set authentication list for enable. eou Set authentication lists for EAPoUDP fail-message Message to use for failed login/authentication. login Set authentication lists for logins. onep Set authentication lists for ONEP password-prompt Text to use when prompting for a password ppp Set authentication lists for ppp. sgbp Set authentication lists for sgbp. suppress Do not send access request for a specific type of user. username-prompt Text to use when prompting for a username 3750X(config)#aaa authentication dot1x ? WORD Named authentication list (max 31 characters, longer will be rejected). default The default authentication list. 3750X(config)#aaa authentication dot1x default ? cache Use Cached-group group Use Server-group local Use local username authentication. 3750X(config)#aaa authentication dot1x default group ? WORD Server-group name ldap Use list of all LDAP hosts. radius Use list of all Radius hosts. 3750X(config)#aaa authentication dot1x default group ISE ? cache Use Cached-group group Use Server-group local Use local username authentication.There are a few ISE-specific commands we need, some attrributes, some "lockdown" - so we make sure that we send requests from the correct source interface, and finally to turn on dot1x:3750X(config)#aaa authentication dot1x default group ISE local ? cache Use Cached-group group Use Server-group 3750X(config)#aaa authentication dot1x default group ISE local 3750X(config)#aaa authorization ? auth-proxy For Authentication Proxy Services cache For AAA cache configuration commands For exec (shell) commands. config-commands For configuration mode commands. configuration For downloading configurations from AAA server console For enabling console authorization credential-download For downloading EAP credential from Local/RADIUS/LDAP exec For starting an exec (shell). multicast For downloading Multicast configurations from an AAA server network For network services. (PPP, SLIP, ARAP) onep For ONEP authorization service policy-if For diameter policy interface application. prepaid For diameter prepaid services. radius-proxy For proxying radius packets reverse-access For reverse access connections subscriber-service For iEdge subscriber services (VPDN etc) template Enable template authorization 3750X(config)#aaa authorization network ? WORD Named authorization list (max 31 characters, longer will be rejected). default The default authorization list. 3750X(config)#aaa authorization network default ? cache Use Cached-group group Use server-group. if-authenticated Succeed if user has authenticated. local Use local database. none No authorization (always succeeds). 3750X(config)#aaa authorization network default group ISE ? cache Use Cached-group group Use server-group. if-authenticated Succeed if user has authenticated. local Use local database. none No authorization (always succeeds). 3750X(config)#aaa authorization network default group ISE local 3750X(config)#aaa accounting ? auth-proxy For authentication proxy events. commands For exec (shell) commands. connection For outbound connections. (telnet, rlogin) delay-start Delay PPP Network start record until peer IP address is known. dot1x For dot1x sessions. exec For starting an exec (shell). gigawords 64 bit interface counters to support Radius attributes 52 & 53. identity For identity sessions. include Include attributes in accounting records unconditionally jitter Set jitter parameters for periodic interval multicast For multicast accounting. nested When starting PPP from EXEC, generate NETWORK records before EXEC-STOP record. network For network services. (PPP, SLIP, ARAP) redundancy AAA platform redundancy accounting behavior send Send records to accounting server. session-duration Set the preference for calculating session durations suppress Do not generate accounting records for a specific type of user. system For system events. update Enable accounting update records. vrrs For VRRS accounting. 3750X(config)#aaa accounting dot1x default ? start-stop Record start and stop without waiting 3750X(config)#aaa accounting dot1x default start-stop ? broadcast Use Broadcast for Accounting group Use Server-group 3750X(config)#aaa accounting dot1x default start-stop group ISE 3750X(config)#aaa accounting update periodic 5 3750X(config)#aaa server ? radius Profile for local radius server 3750X(config)#aaa server radius ? dynamic-author Local server profile for RFC 3576 support policy-device Local server profile for RADIUS External Policy Delegation client proxy Local server profile for RADIUS proxy clients sesm Local server profile for a SESM client 3750X(config)#aaa server radius dynamic-author 3750X(config-locsvr-da-radius)#client ? Hostname or A.B.C.D IP address of RADIUS client X:X:X:X::X IPv6 address of RADIUS client 3750X(config-locsvr-da-radius)#client 192.168.90.205 ? server-key Specify a RADIUS client server-key vrf Virtual Routing/Forwarding parameters 3750X(config-locsvr-da-radius)#client 192.168.90.205 server-key Radius123 3750X(config-locsvr-da-radius)#
3750X(config)#radius-server attribute ? 11 Filter-Id attribute configuration 188 Num-In-Multilink attribute configuration 218 Address-Pool attribute 25 Class attribute 30 DNIS attribute 31 Calling Station ID 32 NAS-Identifier attribute 4 NAS IP address attribute 44 Acct-Session-Id attribute 55 Event-Timestamp attribute 6 Service-Type attribute 61 NAS-Port-Type attribute configuration 66 Tunnel-Client-Endpoint attribute 67 Tunnel-Server-Endpoint attribute 69 Tunnel-Password attribute 77 Connect-Info attribute 8 Framed IP address attribute 95 NAS IPv6 address attribute list List of Attribute Types nas-port NAS-Port attribute configuration nas-port-id Nas-Port-Id attribute configuration 3750X(config)#radius-server attribute 6 ? mandatory Enforce Service-Type attribute in Access-Accept on-for-login-auth Send attribute 6 in authentication packet support-multiple Support multiple Service-Type values per Radius profile voice Select the Service-Type value for Voice calls; defaults to 12 3750X(config)#radius-server attribute 6 on-for-login-auth 3750X(config)#radius-server attribute 8 ? include-in-access-req Send attribute 8 in access-req packet 3750X(config)#radius-server attribute 8 include-in-access-req 3750X(config)#radius-server attribute 25 ? access-request Access-Request packet 3750X(config)#radius-server attribute 25 access-request ? include Include attribute 3750X(config)#radius-server attribute 25 access-request include 3750X(config)# 3750X(config)#radius-server vsa ? disallow Forbid certain VSA behaviour send Send vendor-specific attributes in requests 3750X(config)#radius-server vsa send ? accounting Send in accounting requests authentication Send in access requests cisco-nas-port Send cisco-nas-port VSA(2)There are a lot of attributes, but the important ones are 6, 8 and 25. Attribute 6 is the service type, which is "login" for dot1x, or "call-check" for MAB. 8 includes the IP address of the endpoint device, and 25 includes the class attribute.3750X(config)#radius-server vsa send accounting 3750X(config)#radius-server vsa send auth 3750X(config)#ip radius source-interface vlan 4 3750X(config)# 3750X(config)# 3750X(config)#dot1x system-auth-control 3750X(config)# 3750X(config)#
Let's fire up the vWLC and see if we can get everything talking...
Turning to the vWLC:
Unfortunately, the ISE doesn't seem to want to talk to anything:
ISE20/admin# ping 10.1.4.152 PING 10.1.4.152 (10.1.4.152) 56(84) bytes of data. --- 10.1.4.152 ping statistics --- 4 packets transmitted, 0 received, 100% packet loss, time 32999ms ISE20/admin# ping 10.1.4.100 PING 10.1.4.100 (10.1.4.100) 56(84) bytes of data. --- 10.1.4.100 ping statistics --- 4 packets transmitted, 0 received, 100% packet loss, time 33000ms ISE20/admin# ping 10.1.4.254 PING 10.1.4.254 (10.1.4.254) 56(84) bytes of data. 64 bytes from 10.1.4.254: icmp_seq=1 ttl=255 time=10.2 ms 64 bytes from 10.1.4.254: icmp_seq=2 ttl=255 time=10.3 ms 64 bytes from 10.1.4.254: icmp_seq=3 ttl=255 time=8.31 ms 64 bytes from 10.1.4.254: icmp_seq=4 ttl=255 time=14.3 ms --- 10.1.4.254 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3019ms rtt min/avg/max/mdev = 8.318/10.816/14.369/2.206 ms ISE20/admin# ping 10.1.4.100 PING 10.1.4.100 (10.1.4.100) 56(84) bytes of data. --- 10.1.4.100 ping statistics --- 4 packets transmitted, 0 received, 100% packet loss, time 33000ms ISE20/admin#Well, nothing that it needs to, that is. A bit frustrating! It could be an issue with the image, the vWLC seems to be happy:
(Cisco Controller) >ping 10.1.4.100 Send count=3, Receive count=2 from 10.1.4.100 (Cisco Controller) >ping 10.1.4.100 Send count=3, Receive count=3 from 10.1.4.100 (Cisco Controller) >ping 192.168.90.200 Send count=3, Receive count=3 from 192.168.90.200 (Cisco Controller) >So..
First plan: Reboot ISE and hope for best.
Second plan: Troubleshoot it a bit.
Third plan: Rebuild using different version (probably 1.4).
Fourth plan, move ISE to ESXi native (and again hope that it works).
I'll be back... New post coming up!





















5 comments
commentsVery helpful! Please, do some labs/examples using the vWLC with different vlans, dhcp proxy etc. I bought the ap 1602 and I trying to do some progress also. I'm studying for CCNP-Sec and some times to CCNA-Wireless. :)
ReplyWill try Marcus. Good luck with the studies!
ReplyExcellent work Stuart!
ReplyMy compliments.
Darby Weaver
Http://www.darbyslogs.blogspot.com
Cheers Darby!
Replynice
Reply