The good news is that ISE is working really well for me, and (the better news for you) that I am running out of ISE-related puns. But here is a picture of Mr. Freeze anyway:
Thinking about it, from purely a lab point-of-view, the Guest portal is probably not that essential. It'll be a virtual lab, so actually testing the wifi will be difficult. However, an IP Phone connected to a laptop (or other device), now there is a viable possibility.
So, that is what we do do next.
Here is the current port configuration:
3750X(config-if)#do sh run int gi 3/0/3 | b interface interface GigabitEthernet3/0/3 description IP Phone switchport access vlan 21 switchport mode access switchport voice vlan 9 authentication event fail action next-method authentication host-mode multi-auth authentication open authentication order dot1x mab authentication priority dot1x mab authentication port-control auto authentication periodic mab dot1x pae authenticator spanning-tree portfast end 3750X(config-if)#Setting up the phone was a bit tricky, it's my first time playing with a Cisco phone, so a little learning curve and lots of Googling, I got thrown off by an couple of "errors" but apparently these can be ignored. I don't need the phone to be 100%, just working enough to allow the phone to get onto the network.
Initially, I could not get it working on VLAN 21 (for the data port), but that was due to forgetting to add the necessary VIFs to SW1 and SW2 (because of the rebuild a couple of days ago). Once I had the brainwave that this was the missing component, whilst bathing the twins, and confirming this was the case, a quick fix and the correct VLAN is now being used. As a side note, UNetLab works really well on a Kindle Fire 10, and SSH works well through JuiceSSH. I have not tried VNC integration yet though.
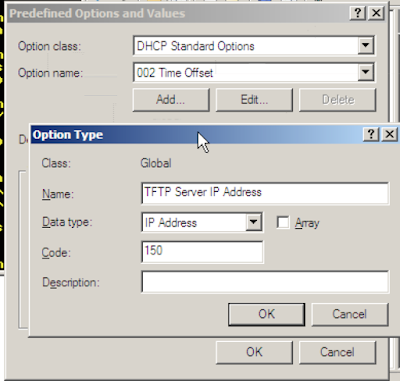
For the phone to work, we need a few things. It needs to be pointed to a TFTP server, and this is done by adding an option in DHCP. In the DHCP server, right-click on IPv4 and select "Set Predefined Options", then click on add and add the following:
Once this is added, under the scope we add the option and point it to the TFTP server:
The VLAN VIF does need the "ip helper-address" command to point to the DHCP server, but this is it as far as DHCP goes.
The TFTP server needs a few files. Naturally we need the firmware files, and I am using 7.5.0. I did try 8.X, but whilst troubleshooting decided to downgrade (in case I was going too high).
The other files are the OS79XX file (as I am using a 7940 IP phone). This needs to have one line, which is the firmware version:
This file gets called first, then the phone looks for another couple of files. We have the SIPDefault.cnf file:
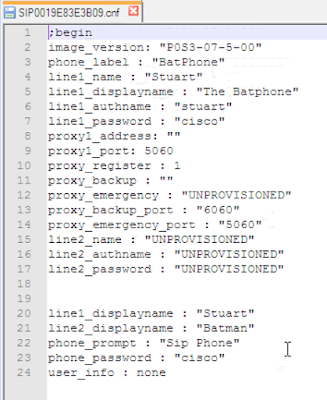
Not sure if the proxy stuff is needed, this was added for troubleshooting. The we have the phone-specific config file, which needs to be named SIPMACADDRESS.cnf, where MACADDRESS is the MAC address of the phone:
The we have the xmlDefault.cnf.xml file, not sure if this is necessary for the 7940 or not, but I have it anyway:
The phone does say thats it's still "unprovisioned", but this is related to the proxy_backup and proxy_emergency commands. This is not a show stopper, but I did send a long time chasing this one.
The phone now connects happily, as does the laptop connected to it:
Let's return to ISE and see what that tells us.
We get a green tick, but not a whole lot else. So, are we missing something?
The Live Log is rather useful here:
3750X#sh authentication interface gi 3/0/3
Client list:
Interface MAC Address Method Domain Status Session ID
Gi3/0/3 e411.5b25.c2e9 dot1x DATA Authz Success 0A01013200000038021D78F6
Gi3/0/3 0019.e83e.3b09 mab VOICE Authz Success 0A01013200000039021D8F8A
Available methods list:
Handle Priority Name
3 0 dot1x
4 1 mab
Runnable methods list:
Handle Priority Name
3 0 dot1x
4 1 mab
3750X#
So, the phone uses MAB (Mac Authentication Bypass) and the laptop uses dot1x. It's good to know that these both work as it's the only reason I bought the 3750X switch.The cool thing is that we can confirm that naughty old Bob is hitting the right policy when using the laptop:
Still making really good headway now. ISE is pretty intuitive, most of the hard stuff is remembering what to add on the actual network devices. Most of the commands either begin with an A (aaa), R (radius) or d (dot1x). Remember this and the rest can probably be figured out through a decent bit of context-sensitive help. But do check out the post on troubleshooting ISE, as that's a real bonus in getting things to work!
We have not really pushed the boundaries though. ISE is a big product with lots of options, so what else can we do? We could do something like permit some traffic, and deny others, using a downloadable ACL.
To create a downloadable ACL we go to Policy > Policy Elements > Results >Authorization > Downloadable ACLs:
We can check the syntax as well, which is a useful feature.
We then need to turn this into something we can use, by creating an Authorization profile:
Now we should be able to attach this to the Bob-Wired-OK policy (and now I am pleased that I created this):
How does this fair?
Well, Bob can still reach the server via HTTP and HTTPS, but the dACL is being used:
Line 11022 shows that the dACL is being sent, it's just not being used by the client. Let's eliminate the phone from the equation and move the laptop to gi3/0/20:
3750X#sh access-list
Extended IP access list Auth-Default-ACL-OPEN
10 permit ip any any (3318 matches)
Extended IP access list xACSACLx-IP-Deny-AP-DNS-to-Bob-5757323f (per-user)
10 deny tcp any host 10.1.4.101 eq www
20 deny tcp any host 10.1.4.101 eq 443
30 permit ip any any
Extended IP access list xACSACLx-IP-PERMIT_ALL_TRAFFIC-56161e32 (per-user)
10 permit ip any any
3750X#sh authentication sessions interface gi3/0/20
Interface: GigabitEthernet3/0/20
MAC Address: e411.5b25.c2e9
IP Address: Unknown
User-Name: dodgybob
Status: Authz Success
Domain: DATA
Security Policy: Should Secure
Security Status: Unsecure
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Policy: N/A
ACS ACL: xACSACLx-IP-Deny-AP-DNS-to-Bob-5757323f
Session timeout: 3600s (local), Remaining: 2836s
Timeout action: Reauthenticate
Idle timeout: N/A
Common Session ID: 0A0101320000004609E58FCD
Acct Session ID: 0x0000005F
Handle: 0x2C000047
Runnable methods list:
Method State
dot1x Authc Success
mab Not run
3750X#
We are definitely getting the right details, the ACL is being applied. I posted yesterday about troubleshooting ISE, so working through that I added as many of the commands as necessary, but still Bob can get to the web page. We also do not see any hits on the access list (which I changed to add the "log" option):
3750X(config-if)#do sh access-lists
Extended IP access list Auth-Default-ACL-OPEN
10 permit ip any any (6511 matches)
Extended IP access list xACSACLx-IP-Deny-AP-DNS-to-Bob-57591fa3 (per-user)
10 deny tcp any host 10.1.4.101 eq www log
20 deny tcp any host 10.1.4.101 eq 443 log
30 permit ip any any log
Extended IP access list xACSACLx-IP-PERMIT_ALL_TRAFFIC-56161e32 (per-user)
10 permit ip any any
3750X(config-if)#
So, I hit the Googles again. Turns out, one of the commands I was missing (ip device tracking) was the one I needed (go figure!):
3750X(config)#ip device tracking
3750X(config)#int gi 3/0/20
3750X(config-if)#shut
3750X(config-if)#no shut
3750X(config-if)#do sh access-lists
Extended IP access list Auth-Default-ACL-OPEN
10 permit ip any any (6531 matches)
Extended IP access list xACSACLx-IP-Deny-AP-DNS-to-Bob-57591fa3 (per-user)
10 deny tcp any host 10.1.4.101 eq www log
20 deny tcp any host 10.1.4.101 eq 443 log
30 permit ip any any log
Extended IP access list xACSACLx-IP-PERMIT_ALL_TRAFFIC-56161e32 (per-user)
10 permit ip any any
3750X(config-if)#
3750X(config-if)#
Now, while the ACL hits do not increment, we do get the desired result. We also fill in one of the blanks in the auth session output (the IP Address):
3750X(config-if)#do sh auth sess int gi 3/0/20
Interface: GigabitEthernet3/0/20
MAC Address: e411.5b25.c2e9
IP Address: 10.1.4.202
User-Name: dodgybob
Status: Authz Success
Domain: DATA
Security Policy: Should Secure
Security Status: Unsecure
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Policy: N/A
ACS ACL: xACSACLx-IP-Deny-AP-DNS-to-Bob-57591fa3
Session timeout: 3600s (local), Remaining: 3420s
Timeout action: Reauthenticate
Idle timeout: 65535s (local), Remaining: 65355s
Common Session ID: 0A0101320000004A0A50A8B8
Acct Session ID: 0x00000070
Handle: 0x4C00004B
Runnable methods list:
Method State
dot1x Authc Success
mab Not run
3750X(config-if)#
3750X(config-if)#do sh ip access-lists int gi 3/0/20
deny tcp host 10.1.4.202 host 10.1.4.101 eq www log
deny tcp host 10.1.4.202 host 10.1.4.101 eq 443 log
permit ip host 10.1.4.202 any log (73 matches)
3750X(config-if)#
So let's move the laptop back to the phone connection, and just make sure that it still does what it is supposed to:
3750X(config-if)#do sh authe sess
Interface MAC Address Method Domain Status Session ID
Gi3/0/3 e411.5b25.c2e9 dot1x DATA Authz Success 0A0101320000004B0A57FC2A
Gi3/0/3 0019.e83e.3b09 mab VOICE Authz Success 0A0101320000003A02750260
3750X(config-if)#do sh authe sess in gi 3/0/3
Interface: GigabitEthernet3/0/3
MAC Address: e411.5b25.c2e9
IP Address: 10.1.21.20
User-Name: dodgybob
Status: Authz Success
Domain: DATA
Security Policy: Should Secure
Security Status: Unsecure
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
Vlan Policy: N/A
ACS ACL: xACSACLx-IP-Deny-AP-DNS-to-Bob-57591fa3
Session timeout: 3600s (local), Remaining: 3582s
Timeout action: Reauthenticate
Idle timeout: 65535s (local), Remaining: 65518s
Common Session ID: 0A0101320000004B0A57FC2A
Acct Session ID: 0x00000071
Handle: 0x2600004C
Runnable methods list:
Method State
dot1x Authc Success
mab Not run
----------------------------------------
Interface: GigabitEthernet3/0/3
MAC Address: 0019.e83e.3b09
IP Address: 10.1.9.20
User-Name: 00-19-E8-3E-3B-09
Status: Authz Success
Domain: VOICE
Security Policy: Should Secure
Security Status: Unsecure
Oper host mode: multi-auth
Oper control dir: both
Authorized By: Authentication Server
ACS ACL: xACSACLx-IP-PERMIT_ALL_TRAFFIC-56161e32
Session timeout: 3600s (local), Remaining: 1318s
Timeout action: Reauthenticate
Idle timeout: N/A
Common Session ID: 0A0101320000003A02750260
Acct Session ID: 0x00000045
Handle: 0xE800003B
Runnable methods list:
Method State
dot1x Failed over
mab Authc Success
3750X(config-if)#
Bob still cannot get to the 10.1.4.101 web page by HTTP or HTTPS. I call that a success! So, what's next? What can we do with ISE? I am kinda tempted to set up the portal for guest access, but not sure if I really need to, maybe we should look at MAB instead.Yep, let's look at MAB, but let's have a new post for that.