I am nearly at the stage for configuring the ASAs in my CCIE Security lab, well, the HQ part at least.
Before we do that though it would probably be a good idea to go through some of the more basic aspects of the Cisco ASA firewall.
Cisco ASA firewall fundamentals
Cisco ASA models
Cisco ASAs come in a two flavors, physical and virtual. The virtual one is relatively new, and is known as the ASAv ("v" for virtual, it makes sense). The physical range of ASA firewalls (5500 series) has been around for a number of years, and replaced the PIX firewalls.
The current product range starts with the 5505, which would be your typical SOHO router firewall combo, and then the range moves into the -X models, starting with the 5506-X.
The X denotes that these models are the next-generation of ASA, and come with FirePOWER, which we'll look at in a different post. So, what is the difference between the 5505 and the 5506-X? It's pretty big actually.
Despite the minor number jump, the 5506 is a far more uprated device. Here are some of the comparative stats from the Cisco website:
Cisco ASA Model
|
ASA 5505 / Security Plus
|
ASA 5506-X / Security Plus
|
| Image |
|
|
| Stateful inspection throughput (max) |
Up to 150 Mbps |
750 Mbps |
| Maximum concurrent sessions |
10,000 / 25,000 |
20,000/50,000 |
| Packets per second (64 byte) |
85,000 |
246,900 |
| Maximum site-to-site and IPsec IKEv1 client VPN user sessions |
10 / 25 |
10 / 50 |
| Maximum Cisco AnyConnect IKEv2 remote access VPN or clientless VPN user sessions |
25 |
2 / 50 |
| VLANs |
3 (trunking disabled) / 20 (trunking enabled) |
5 / 30 |
| High-availability support |
Stateless A/S only (active / standby) |
A / S |
| Integrated I/O |
8-port FE with 2 Power over Ethernet (PoE) ports |
8 x 1 Gigabit Ethernet (GE) |
As you can see, you can push a far greater amount of traffic through the 5506-X than the 5505.
Prices for the 5505 start at about £250, and go up to around £800, the one above falls into the latter price range. The 5506-X range is not much more expensive, prices start at around £400.
As you move higher up the model line, naturally the prices start to enter enterprise kind of money (lots of zeros at the end). But, again, you do get more bang for your buck.
Sizing a firewall is tricky business. You need to look at the number of users you have, both on site and remote, the number that will be connecting via VPN, both site to site, and client VPN, such as AnyConnect. You also need to look at what kind of application traffic the firewall will be passing.
For example the 5512-X could easily support around 2000 users, with around 500 of those being remote users. Prices for this are around £2300.
Basic Cisco ASA firewall configuration
Cisco ASA firewalls are anything but basic. But don't be put off by their complexity. Getting them up and running can be done in a short space of time.
Let's start off with our interfaces, and how they relate to firewall function. A firewall separates traffic between different areas. The ASA interfaces can be assigned to different areas, we will need one on the outside, connecting us to our upstream service provider, one on the inside for our users, and maybe one for our public facing servers, which is known as a DMZ, or Demilitarised Zone.
In our example below, we have an ISP, our ASA (ASAv), and our client (user) machine:
We will, for a little while, need to use VNC to control the ASA.
Our Gi0/0 interface will be our "Outside" interface, and our Gi0/1 interface will be our "Inside" interface. There is a reason we name them these, and that is because the ASA will automatically assign a security level to these interfaces, as we will see in a moment.
Let's get started.
ISP:
Router(config)#ho ISP
ISP(config)#int fa0/0
ISP(config-if)#ip add 10.1.1.1 255.255.255.252
ISP(config-if)#no shu
ISP(config-if)#int lo0
ISP(config-if)#ip add 8.8.8.8 255.255.255.255
ISP(config-if)#ip route 0.0.0.0 0.0.0.0 10.1.1.2
ISP(config)#
User-PC:
Router(config)#ho User1
User1(config)#int fa0/0
User1(config-if)#ip add 192.168.1.17 255.255.255.0
User1(config-if)#no shu
User1(config-if)#ip route 0.0.0.0 0.0.0.0 192.168.1.254
User1(config)#
Cisco ASA interface configuration
OK, let's configure the ASA up, starting with setting the hostname and the outside interface:
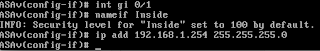
Now we configure the Inside interface:
Notice how the ASA will set the security levels according to the interface names, with 0 for the Outside interface, and 100 for the Inside interface. 0 is a "least trusted" level and 100 is the "most trusted" level. We can set these manually if we want to, using the command "security-level <0-100>".
At this stage we should have connectivity from the User1 "PC", and from the ISP:
User1#ping 192.168.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.254, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/7/12 ms
User1#
ISP#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/12/28 ms
ISP#
The ASAv needs to be aware of the 8.8.8.8 "server", so we can create a default route on the ASAv to do this:
Notice that unlike traditional IOS based devices, the ASA is actually a little less clever here, we need to specify the interface, or direction, that the route affects.
Allowing SSH access to Cisco ASA
Now, let's set ourselves up to manage the ASA from our User1 "PC". Firstly we need to generate our general-keys, using the command "crypto key generate rsa modulus 1024", ideally (in production), you should use 2048:
Notice that I also set the domain name, and the version.
The rest of the commands are being shown through show commands, once I have successfully connected from User1:
User1#ssh -l stu 192.168.1.254
Password:
Type help or '?' for a list of available commands.
ASAv> en
Password: ******
ASAv# sh run | i username
username stu password QFwZO2R.a0n6RaA/ encrypted privilege 15
ASAv# sh run | i aaa
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
ASAv# sh run | i ssh
aaa authentication ssh console LOCAL
ssh stricthostkeycheck
ssh 192.168.1.0 255.255.255.0 Inside
ssh timeout 5
ssh version 2
ssh key-exchange group dh-group1-sha1
ASAv# sh run | i management
management-only
management-access Inside
ASAv#
We will need a user to connect with. Notice the the password gets automatically encrypted. We have two AAA commands, one for SSH access, another for enable level access. We also enable ssh access from the 192.168.1.0/24 subnet, and have allowed management access from anything behind the Inside interface.
Now we can work a little easier. The final step it to get the User1 PC to access the 8.8.8.8 server out on the Internet. To do this the ASA needs to perform a bit of Network Address Translation (NAT).
Internet access for inside hosts on a Cisco ASA
Let's give access for our inside hosts. To do this does not take many steps, we just need to create a network to match everything, and then NAT this:
ASAv(config)# object network OBJ_OUTSIDE
ASAv(config-network-object)# subnet 0.0.0.0 0.0.0.0
ASAv(config-network-object)# exi
ASAv(config)# nat (Inside,Outside) source dynamic OBJ_OUTSIDE interface
ASAv(config)#
Although ping does not work, telnet does:
ASAv(config)# exi
ASAv# exi
[Connection to 192.168.1.254 closed by foreign host]
User1#ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
User1#telnet 8.8.8.8
Trying 8.8.8.8 ... Open
Password required, but none set
[Connection to 8.8.8.8 closed by foreign host]
User1#
We can prove that this works, by setting a password on the ISP router:
ISP(config)#line vty 0 4
ISP(config-line)#password 802101
ISP(config-line)#exi
ISP(config)#enable password 802101
ISP(config)#
User1#telnet 8.8.8.8
Trying 8.8.8.8 ... Open
User Access Verification
Password:
ISP>en
Password:
ISP#who
Line User Host(s) Idle Location
0 con 0 idle 00:00:24
* 2 vty 0 idle 00:00:00 10.1.1.2
Interface User Mode Idle Peer Address
ISP#
So, you can see that the ASAv has performed NAT for User1. We can check this on the ASAv:
So, telnet worked fine, what about http requests? Well, the ASAv will perform NAT (well, PAT to be precise) for us. We can see this by setting up the ISP router to be an HTTP server:
ISP(config)#ip http server
ISP(config)#
User1#telnet 8.8.8.8 80
Trying 8.8.8.8, 80 ... Open
get
HTTP/1.1 400 Bad Request
Date: Sat, 05 Sep 2015 14:28:30 GMT
Server: cisco-IOS
Accept-Ranges: none
400 Bad Request
[Connection to 8.8.8.8 closed by foreign host]
User1#
As you can see, it does not take long to get up and running with an ASA. Now that we have had our little introduction to ASAs, I can start configuring them up in my lab (in a day or two).