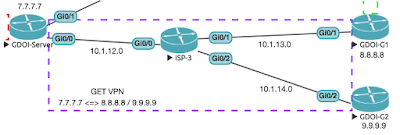
GET VPN or Group Encrypted Transport is next in the list of VPNs to cover.
Much of the configuration will be the same as we have seen before (ISAKMP policies, transform sets, IPSec profiles), but some will be quite new (GDOI groups).
Before we start with the fun stuff, we'll need to set up the basic connectivity (and it will be very basic):
GDOI-Server(config)#router ospf 1 GDOI-Server(config-router)#router-id 7.7.7.7 GDOI-Server(config-router)#network 10.1.12.0 0.0.0.255 area 1 GDOI-Server(config-router)# *Jul 5: %OSPF-4-NOVALIDKEY: No valid authentication send key is available on interface GigabitEthernet0/0 GDOI-Server(config-router)#int gi 0/0 GDOI-Server(config-if)#ip ospf auth mess GDOI-Server(config-if)#ip ospf mess 1 md5 cisco GDOI-Server(config-if)# ISP-3(config)#router ospf 1 ISP-3(config-router)#router-id 10.1.12.1 ISP-3(config-router)#area 1 auth mess ISP-3(config-router)#network 10.1.12.0 0.0.0.255 area 1 ISP-3(config-router)#network 10.1.13.0 0.0.0.255 area 1 ISP-3(config-router)#network 10.1.14.0 0.0.0.255 area 1 ISP-3(config-router)# ISP-3(config-router)#int rang ISP-3(config-router)#int rang gi 0/0 - 2 ISP-3(config-if-range)#ip ospf auth messa ISP-3(config-if-range)#ip ospf mess 1 md5 cisco ISP-3(config-if-range)# GDOI-G1(config)#router ospf 1 GDOI-G1(config-router)#router-id 8.8.8.8 GDOI-G1(config-router)#network 10.1.13.0 0.0.0.255 area 1 GDOI-G1(config-router)#area 1 authe mess GDOI-G1(config-router)#network 8.8.8.8 0.0.0.0 area 1 GDOI-G1(config-router)# GDOI-G1(config-router)#int gi 0/0 GDOI-G1(config-if)#int gi 0/1 GDOI-G1(config-if)#ip ospf auth mess GDOI-G1(config-if)#ip ospf mess 1 md5 cisco GDOI-G1(config-if)# *Jul 5: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.12.1 on GigabitEthernet0/1 from LOADING to FULL, Loading Done GDOI-G1(config-if)# GDOI-G2(config)#router ospf 1 GDOI-G2(config-router)#router-id 9.9.9.9 GDOI-G2(config-router)#network 9.9.9.9 0.0.0.0 a 1 GDOI-G2(config-router)#network 10.1.14.0 0.0.0.255 area 1 GDOI-G2(config-router)#area 1 auth mess GDOI-G2(config-router)#int gi 0/2 GDOI-G2(config-if)#ip ospf auth mess GDOI-G2(config-if)#ip os mess 1 md cisco GDOI-G2(config-if)# *Jul 5: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.12.1 on GigabitEthernet0/2 from LOADING to FULL, Loading Done GDOI-G2(config-if)# GDOI-Server#ping 8.8.8.8 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 7.7.7.7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/5 ms GDOI-Server#ping 9.9.9.9 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 9.9.9.9, timeout is 2 seconds: Packet sent with a source address of 7.7.7.7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/5/7 ms GDOI-Server#OK, let's begin in the same way as we did with dual-hub DMVPN, and chuck the basics into notepad and paste then into the routers:
crypto isakmp policy 10 encryption 3des authentication pre-share hash sha group 2 crypto isakmp key cisco address 0.0.0.0 0.0.0.0 crypto ipsec transform-set GET-TS esp-3des esp-sha-hmac exit crypto ipsec profile GET-Profile set transform-set GET-TS exitThis time, I put the commands on the GDOI-Server router first, then copied them to notepad and pasted into the clients, this way it means that any fat-fingering will be picked up on quicker, and not transferred to the clients:
GDOI-G1(config)#crypto isakmp policy 10 GDOI-G1(config-isakmp)#encryption 3des GDOI-G1(config-isakmp)#authentication pre-share GDOI-G1(config-isakmp)#hash sha GDOI-G1(config-isakmp)#group 2 GDOI-G1(config-isakmp)#crypto isakmp key cisco address 0.0.0.0 0.0.0.0 GDOI-G1(config)#crypto ipsec transform-set GET-TS esp-3des esp-sha-hmac GDOI-G1(cfg-crypto-trans)#exit GDOI-G1(config)#crypto ipsec profile GET-Profile GDOI-G1(ipsec-profile)#set transform-set GET-TS GDOI-G1(ipsec-profile)#exit GDOI-G1(config)# GDOI-G2(config)#crypto isakmp policy 10 GDOI-G2(config-isakmp)#encryption 3des GDOI-G2(config-isakmp)#authentication pre-share GDOI-G2(config-isakmp)#hash sha GDOI-G2(config-isakmp)#group 2 GDOI-G2(config-isakmp)#crypto isakmp key cisco address 0.0.0.0 0.0.0.0 GDOI-G2(config)#crypto ipsec transform-set GET-TS esp-3des esp-sha-hmac GDOI-G2(cfg-crypto-trans)#exit GDOI-G2(config)#crypto ipsec profile GET-Profile GDOI-G2(ipsec-profile)#set transform-set GET-TS GDOI-G2(ipsec-profile)#exitNow, let's head back to the server and see what GET VPN has in store. I will be making heavy use of the context-sensitive help here, and putting notes in the output:
GDOI-Server(config)#crypto gdoi ?
group Configure a GKM (Group Key Management, GDOI or G-IKEv2) Group
GDOI-Server(config)#crypto gdoi group ?
WORD Group Name
ipv6 IPv6 GKM (Group Key Management) Group
GDOI-Server(config)#crypto gdoi group GDOI-G1
GDOI-Server(config-gkm-group)#?
GKM (Group Key Management) Group configuration commands:
client Set the group dsclient parameters
default Set a command to its defaults
exit Exit the group mode
identity Set the identity of the group
no Negate a command or set its defaults
passive Set the group in passive mode
server Set the group server for of the group
GDOI-Server(config-gkm-group)#server ?
address Identify the group server by address
hostname Identify the group server by hostname
local Configure GKM group server defined locally
GDOI-Server(config-gkm-group)#server local ?
GDOI-Server(config-gkm-group)#server local
GDOI-Server(gkm-local-server)#
*Jul 5: %CRYPTO-6-GDOI_ON_OFF: GDOI is ON
GDOI-Server(gkm-local-server)#address ?
ipv4 Set ipv4 address of local server
GDOI-Server(gkm-local-server)#address ipv4 ?
A.B.C.D IPv4 local address
GDOI-Server(gkm-local-server)#address ipv4 7.7.7.7
GDOI-Server(gkm-local-server)#sa ?
d3p Enable IP delivery delay detection protocol for all SAs
within the group
ipsec Configure an IPsec SA
pair-wise-keying Enable KGS pair-wise-keying
receive-only Configure SA to work only in inbound direction
GDOI-Server(gkm-local-server)#sa ipsec ?
Sequence to insert into SA list
GDOI-Server(gkm-local-server)#sa ipsec 1
GDOI-Server(gkm-sa-ipsec)#?
GKM local server IPsec SA configuration commands:
default Set a command to its defaults
exit Exit the sa ipsec mode
match Match characteristics of packets to encrypt
no Negate a command or set its defaults
profile Configure an ipsec profile for the SA
replay Set replay method
tag Set inline tagging method
GDOI-Server(gkm-sa-ipsec)#profile GET-Profile
GDOI-Server(gkm-sa-ipsec)#match ?
address Match addresses of packets to encrypt
GDOI-Server(gkm-sa-ipsec)#match address ?
ipv4 Match ipv4 packets
ipv6 Match ipv6 packets
GDOI-Server(gkm-sa-ipsec)#match address ipv4 ?
IP access-list number
IP access-list number (expanded range)
WORD Access-list name
GDOI-Server(gkm-sa-ipsec)#match address ipv4 G1
GDOI-Server(gkm-sa-ipsec)#exit
GDOI-Server(gkm-local-server)#exit
GDOI-Server(config-gkm-group)#end
GDOI-Server#sh run
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 0.0.0.0
crypto ipsec transform-set GET-TS esp-3des esp-sha-hmac
mode tunnel
crypto ipsec profile GET-Profile
set transform-set GET-TS
crypto gdoi group GDOI-G1
identity number 1
server local
sa ipsec 1
! Incomplete
! Match address is not configured
profile GET-Profile
match address ipv4 G1
replay counter window-size 64
no tag
address ipv4 7.7.7.7
GDOI-Server#
One thing I do find very useful is that the IOS will tell me what I am missing. It doesn't do this for everything (it's not a mind-reader), but here it is very useful and shows me that the gdoi group is incomplete, and I am missing a match address statement. Let's fix that by permitting our overlay IP address (VPN range, like we have in DMVPN):GDOI-Server(config)#ip access-list extended G1 GDOI-Server(config-ext-nacl)#remark Probably our VPN IP range GDOI-Server(config-ext-nacl)#permit ip 192.168.2.0 0.0.0.255 192.168.2.0 0.0.0.255 GDOI-Server(config-ext-nacl)#do sh run | s crypto gdoi crypto gdoi group GDOI-G1 identity number 1 server local sa ipsec 1 profile GET-Profile match address ipv4 G1 replay counter window-size 64 no tag address ipv4 7.7.7.7 GDOI-Server(config-ext-nacl)#! better! GDOI-Server(config-ext-nacl)#Makes sense really! Let's have a look at a few show commands:
GDOI-Server#sh crypto gdoi group GDOI-G1
Group Name : GDOI-G1 (Multicast)
Re-auth on new CRL : Disabled
Group Identity : 1
Group Type : GDOI (ISAKMP)
Crypto Path : ipv4
Key Management Path : ipv4
Group Members : 0
IPSec SA Direction : Both
Group Rekey Lifetime : 86400 secs
Rekey Retransmit Period : 10 secs
Rekey Retransmit Attempts: 2
IPSec SA Number : 1
IPSec SA Rekey Lifetime: 3600 secs
Profile Name : GET-Profile
Replay method : Count Based
Replay Window Size : 64
Tagging method : Disabled
ACL Configured : access-list G1
Group Server list : Local
GDOI-Server#sh crypto gdoi ks
Total group members registered to this box: 0
Key Server Information For Group GDOI-G1:
Group Name : GDOI-G1
Re-auth on new CRL : Disabled
Group Identity : 1
Group Type : GDOI (ISAKMP)
Group Members : 0
Rekey Acknowledgement Cfg: Cisco
IPSec SA Direction : Both
CKM status : Disable
ACL Configured:
access-list G1
GDOI-Server#
GDOI-Server#sh crypto gdoi
GROUP INFORMATION
Group Name : GDOI-G1 (Multicast)
Re-auth on new CRL : Disabled
Group Identity : 1
Group Type : GDOI (ISAKMP)
Crypto Path : ipv4
Key Management Path : ipv4
Group Members : 0
IPSec SA Direction : Both
Group Rekey Lifetime : 86400 secs
Rekey Retransmit Period : 10 secs
Rekey Retransmit Attempts: 2
IPSec SA Number : 1
IPSec SA Rekey Lifetime: 3600 secs
Profile Name : GET-Profile
Replay method : Count Based
Replay Window Size : 64
Tagging method : Disabled
ACL Configured : access-list G1
Group Server list : Local
GDOI-Server#
Nothing registered yet, but thats not surprising as we have not configured any client. Let's create the second group:GDOI-Server(config)#crypto gdoi group GDOI-G2 GDOI-Server(config-gkm-group)#identity number 2 GDOI-Server(config-gkm-group)#server local GDOI-Server(gkm-local-server)#sa ipsec 1 GDOI-Server(gkm-sa-ipsec)#profile GET-Profile GDOI-Server(gkm-sa-ipsec)#match address ipv4 G2 GDOI-Server(gkm-sa-ipsec)#replay counter window-size 64 GDOI-Server(gkm-sa-ipsec)#no tag GDOI-Server(gkm-sa-ipsec)#exit GDOI-Server(gkm-local-server)#address ipv4 7.7.7.7 GDOI-Server(gkm-local-server)#exit GDOI-Server(config-gkm-group)#exit GDOI-Server(config)#ip access-list extended G2 GDOI-Server(config-ext-nacl)#permit ip 192.168.3.0 0.0.0.255 192.168.3.0 0.0.0.255 GDOI-Server(config-ext-nacl)#exit GDOI-Server(config)#do sh run | s crypto gdoi crypto gdoi group GDOI-G1 identity number 1 server local sa ipsec 1 profile GET-Profile match address ipv4 G1 replay counter window-size 64 no tag address ipv4 7.7.7.7 crypto gdoi group GDOI-G2 identity number 2 server local sa ipsec 1 profile GET-Profile match address ipv4 G2 replay counter window-size 64 no tag address ipv4 7.7.7.7 GDOI-Server(config)#OK, I have kind of bumbled my way through that, but let's see if we can get one of the clients to connect...
GDOI-G1(config)#crypto gdoi group GDOI-G1
GDOI-G1(config-gkm-group)#?
GKM (Group Key Management) Group configuration commands:
client Set the group client parameters
default Set a command to its defaults
exit Exit the group mode
identity Set the identity of the group
no Negate a command or set its defaults
passive Set the group in passive mode
server Set the group server for of the group
GDOI-G1(config-gkm-group)#server ?
address Identify the group server by address
hostname Identify the group server by hostname
local Configure GKM group server defined locally
GDOI-G1(config-gkm-group)#server address ?
ipv4 Set the IPv4 address of the group server
GDOI-G1(config-gkm-group)#server address ipv4 ?
A.B.C.D Group server IPv4 address
GDOI-G1(config-gkm-group)#server address ipv4 7.7.7.7
GDOI-G1(config-gkm-group)#identity ?
address Set the identity of the group as an address
number Set the identity of the group as a number
GDOI-G1(config-gkm-group)#identity number 1
GDOI-G1(config-gkm-group)#exit
GDOI-G1(config)#crypto isakmp profile GET-Profile
GDOI-G1(conf-isa-prof)#match ?
certificate Peer certificate attributes
identity Peer identity
GDOI-G1(conf-isa-prof)#match identity ?
address IP Address(es)
group Group name
host match a hostname/domain
user-fqdn match a username/domain
GDOI-G1(conf-isa-prof)#match identity address ?
A.B.C.D IP address prefix
ipv6 IPv6 Address(es)
GDOI-G1(conf-isa-prof)#match identity address 7.7.7.7
GDOI-G1(conf-isa-prof)#exit
GDOI-G1(config)#crypto map GDOI-G1 isakmp-profile GET-Profile
GDOI-G1(config)#crypto map G1 10 gdoi
% NOTE: This new crypto map will remain disabled until a valid
group has been configured.
GDOI-G1(config-crypto-map)#set group GDOI-G1
GDOI-G1(config-crypto-map)#int gi0/1
GDOI-G1(config-if)#crypto ?
ipsec Set IPSec parameters
map Assign a Crypto Map
GDOI-G1(config-if)#crypto map ?
WORD Crypto Map tag
GDOI-G1(config-if)#crypto map G1
GDOI-G1(config-if)#
*Jul 5: %CRYPTO-6-GDOI_ON_OFF: GDOI is ON
*Jul 5: %CRYPTO-5-GM_REGSTER: Start registration to KS 7.7.7.7 for group GDOI-G1 using address 10.1.13.8 fvrf default ivrf default
*Jul 5: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Main mode failed with peer at 7.7.7.7
GDOI-G1(config-if)#
GDOI-G1(config-if)#
*Jul 5: %CRYPTO-4-IKMP_NO_SA: IKE message from 7.7.7.7 has no SA and is not an initialization offer
*Jul 5: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Main mode failed with peer at 7.7.7.7
OK... some issues here. Let's try setting the client interface:GDOI-G1(config)#crypto gdoi group GDOI-G1
GDOI-G1(config-gkm-group)#client ?
bypass-policy Allow group-key management traffic sent to this GM
only
protocol Group Member Registration & Rekey Protocol
recovery-check Specify GM recovery check parameters
registration Set the group client management/register interface
rekey Set the group client acceptable rekey ciphers and
hashs
status group-member status
transform-sets Specify list of group client acceptable transform sets
transport-encrypt-key Enforce group or pair-wise keying
GDOI-G1(config-gkm-group)#client registration interface gi0/1
Still no dice, but then I left out a whole load of possible commands for the rekey. This blog post is pretty useful, and kind of mirrors the same set-up that I have. So let's add the rekey information and see if that helps.GDOI-Server(config)#crypto gdoi group GDOI-G1 GDOI-Server(config-gkm-group)#server local GDOI-Server(gkm-local-server)# rekey retransmit 10 number 3 GDOI-Server(gkm-local-server)# rekay authentication mypubkey rsa GDOI-Server-Key GDOI-Server(gkm-local-server)# rekey transport unicastI am still seeing the same errors on GDOI-G1 though. I think, from reading the post linked above, that this may be due to the ACL being incorrect. Unlike the other VPN solutions, we are not overlaying, and by this, I mean that in "standard" tunnels, we have a separate IP addressing scheme, such as the 192.168.1.0/24 subnet we used with DMVPN. GETVPN doesn't work like this, so let's change the ACL and permit the subnets. The interesting thing about GET VPN (well, GDOI to be exact) is that the Key Server (GDOI-Server in our example), downloads the IPSec policy to the GMs (Group members, which are GDOI-G1 and GDOI-G2). In this ACL we define the traffic we need to encrypt, but also the traffic which needs to excluded (OSPF and the GETVPN traffic, UDP port 848). We can have different ACLs per group, so we now get something along the lines of:
ip access-list extended G1 no permit ip 192.168.2.0 0.0.0.255 192.168.2.0 0.0.0.255 deny udp any eq 848 any eq 848 deny tcp any host 224.0.0.5 deny tcp any host 224.0.0.6 permit ip 10.1.12.0 0.0.0.255 10.1.13.0 0.0.0.255 ip access-list extended G2 no permit ip 192.168.3.0 0.0.0.255 192.168.3.0 0.0.0.255 deny udp any eq 848 any eq 848 deny tcp any host 224.0.0.5 deny tcp any host 224.0.0.6 permit ip 10.1.12.0 0.0.0.255 10.1.14.0 0.255.255.255Even with the change in ACL the same errors occurred. It was only when switching to the physical interface on the GDOI-Server, that there was some success:
GDOI-Server(config)#crypto gdoi group GDOI-G1
GDOI-Server(config-gkm-group)#server local
GDOI-Server(gkm-local-server)#address ipv4 10.1.12.7
GDOI-G1#sh crypto gdoi
GROUP INFORMATION
Group Name : GDOI-G1
Group Identity : 1
Group Type : GDOI (ISAKMP)
Crypto Path : ipv4
Key Management Path : ipv4
Rekeys received : 2
IPSec SA Direction : Both
Group Server list : 10.1.12.7
Group Member Information For Group GDOI-G1:
IPSec SA Direction : Both
ACL Received From KS : gdoi_group_GDOI-G1_temp_acl
Group member : 10.1.13.8 vrf: None
Local addr/port : 10.1.13.8/848
Remote addr/port : 10.1.12.7/848
fvrf/ivrf : None/None
Version : 1.0.12
Registration status : Registered
Registered with : 10.1.12.7
Re-registers in : 3366 sec
Succeeded registration: 1
Attempted registration: 1
Last rekey from : 10.1.12.7
Last rekey seq num : 0
Unicast rekey received: 2
Rekey ACKs sent : 2
Rekey Rcvd(hh:mm:ss) : 00:00:08
DP Error Monitoring : OFF
IPSEC init reg executed : 0
IPSEC init reg postponed : 0
Active TEK Number : 2
SA Track (OID/status) : disabled
allowable rekey cipher: any
allowable rekey hash : any
allowable transformtag: any ESP
Rekeys cumulative
Total received : 2
After latest register : 2
Rekey Acks sents : 2
ACL Downloaded From KS 10.1.12.7:
access-list deny udp any port = 848 any port = 848
access-list deny tcp any host 224.0.0.5
access-list deny tcp any host 224.0.0.6
access-list permit ip 10.1.12.0 0.0.0.255 10.1.13.0 0.0.0.255
KEK POLICY:
Rekey Transport Type : Unicast
Lifetime (secs) : 86370
Encrypt Algorithm : 3DES
Key Size : 192
Sig Hash Algorithm : HMAC_AUTH_SHA
Sig Key Length (bits) : 1296
TEK POLICY for the current KS-Policy ACEs Downloaded:
GigabitEthernet0/1:
IPsec SA:
spi: 0x7CD79516(2094503190)
transform: esp-3des esp-sha-hmac
sa timing:remaining key lifetime (sec): (3572)
Anti-Replay(Counter Based) : 64
tag method : disabled
alg key size: 24 (bytes)
sig key size: 20 (bytes)
encaps: ENCAPS_TUNNEL
IPsec SA:
spi: 0x23E7E211(602399249)
transform: esp-3des esp-sha-hmac
sa timing:remaining key lifetime (sec): (152)
Anti-Replay(Counter Based) : 64
tag method : disabled
alg key size: 24 (bytes)
sig key size: 20 (bytes)
encaps: ENCAPS_TUNNEL
GDOI-G1#
GDOI-Server#sh crypto gdoi
GROUP INFORMATION
Group Name : GDOI-G1 (Unicast)
Re-auth on new CRL : Disabled
Group Identity : 1
Group Type : GDOI (ISAKMP)
Crypto Path : ipv4
Key Management Path : ipv4
Group Members : 1
IPSec SA Direction : Both
Group Rekey Lifetime : 86400 secs
Group Rekey
Remaining Lifetime : 86232 secs
Time to Rekey : 85997 secs
Acknowledgement Cfg : Cisco
Rekey Retransmit Period : 10 secs
Rekey Retransmit Attempts: 3
Group Retransmit
Remaining Lifetime : 0 secs
IPSec SA Number : 1
IPSec SA Rekey Lifetime: 3600 secs
Profile Name : GET-Profile
Replay method : Count Based
Replay Window Size : 64
Tagging method : Disabled
SA Rekey
Remaining Lifetime : 3433 secs
Time to Rekey : 3037 secs
ACL Configured : access-list G1
Group Server list : Local
GDOI-Server#
Let's finish off and add the other group in. This time we will set the isakmp profile to match the physical address of the server. This makes more sense, but the G1 router is still using 7.7.7.7, so what will happen?:GDOI-G2(config)#crypto isakmp policy 10
GDOI-G2(config-isakmp)# encr 3des
GDOI-G2(config-isakmp)# authentication pre-share
GDOI-G2(config-isakmp)# hash sha
GDOI-G2(config-isakmp)# group 2
GDOI-G2(config-isakmp)# lifetime 3600
GDOI-G2(config-isakmp)#crypto isakmp key cisco address 10.1.12.7
GDOI-G2(config)#crypto isakmp invalid-spi-recovery
GDOI-G2(config)#crypto isakmp keepalive 10
GDOI-G2(config)#crypto isakmp profile GET-Profile
% A profile is deemed incomplete until it has match identity statements
GDOI-G2(conf-isa-prof)# match identity address 10.1.12.7 255.255.255.255
GDOI-G2(conf-isa-prof)#!
GDOI-G2(conf-isa-prof)#!
GDOI-G2(conf-isa-prof)#$c transform-set GET-TS esp-3des esp-sha-hmac
GDOI-G2(cfg-crypto-trans)# mode tunnel
GDOI-G2(cfg-crypto-trans)#!
GDOI-G2(cfg-crypto-trans)#crypto ipsec profile GET-Profile
GDOI-G2(ipsec-profile)# set transform-set GET-TS
GDOI-G2(ipsec-profile)#!
GDOI-G2(ipsec-profile)#!
GDOI-G2(ipsec-profile)#crypto gdoi group GDOI-G2
GDOI-G2(config-gkm-group)# identity number 2
GDOI-G2(config-gkm-group)# server address ipv4 10.1.12.7
GDOI-G2(config-gkm-group)# client registration interface GigabitEthernet0/2
GDOI-G2(config-gkm-group)#!
GDOI-G2(config-gkm-group)#!
GDOI-G2(config-gkm-group)#crypto map G2 10 gdoi
% NOTE: This new crypto map will remain disabled until a valid
group has been configured.
GDOI-G2(config-crypto-map)# set group GDOI-G2
GDOI-G2(config-crypto-map)#!
GDOI-G2(config-crypto-map)#crypto map GDOI-G2 isakmp-profile GET-Profile
GDOI-G2(config)#!
GDOI-G2(config)#interface GigabitEthernet0/2
GDOI-G2(config-if)# crypto map G2
GDOI-G2(config-if)#
*Jul 6: %CRYPTO-6-GDOI_ON_OFF: GDOI is ON
*Jul 6: %CRYPTO-5-GM_REGSTER: Start registration to KS 10.1.12.7 for group GDOI-G2 using address 10.1.14.9 fvrf default ivrf default
*Jul 6: %CRYPTO-4-IKMP_NO_SA: IKE message from 10.1.12.7 has no SA and is not an initialization offer
GDOI-G2(config-if)#
*Jul 6: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Main mode failed with peer at 10.1.12.7
GDOI-G2(config-if)#
We see the same issues with the SA until we change the match statement in the ipsec profile:GDOI-G2(config)#crypto isakmp profile GET-Profile
GDOI-G2(conf-isa-prof)# match identity address 7.7.7.7 255.255.255.255
GDOI-G2(conf-isa-prof)#no match identity address 10.1.12.7 255.255.255.0
GDOI-G2(conf-isa-prof)#int gi 0/2
GDOI-G2(config-if)#shut
GDOI-G2(config-if)#
*Jul 6: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.12.1 on GigabitEthernet0/2 from FULL to DOWN, Neighbor Down: Interface down or detached
GDOI-G2(config-if)#
*Jul 6: %LINK-5-CHANGED: Interface GigabitEthernet0/2, changed state to administratively down
*Jul 6: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to down
GDOI-G2(config-if)#
GDOI-G2(config-if)#no shut
GDOI-G2(config-if)#
*Jul 6: %LINK-3-UPDOWN: Interface GigabitEthernet0/2, changed state to up
*Jul 6: %CRYPTO-5-GM_REGSTER: Start registration to KS 10.1.12.7 for group GDOI-G2 using address 10.1.14.9 fvrf default ivrf default
*Jul 6: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to up
*Jul 6: %OSPF-5-ADJCHG: Process 1, Nbr 10.1.12.1 on GigabitEthernet0/2 from LOADING to FULL, Loading Done
*Jul 6: %CRYPTO-4-IKMP_NO_SA: IKE message from 10.1.12.7 has no SA and is not an initialization offer
*Jul 6: %GDOI-5-SA_TEK_UPDATED: SA TEK was updated
*Jul 6: %GDOI-5-SA_KEK_UPDATED: SA KEK was updated 0x24FF75BFCD871C9755FE4868CC8A1369
*Jul 6: %GDOI-5-GM_REGS_COMPL: Registration to KS 10.1.12.7 complete for group GDOI-G2 using address 10.1.14.9 fvrf default ivrf default
*Jul 6: %GDOI-5-GM_INSTALL_POLICIES_SUCCESS: SUCCESS: Installation of Reg/Rekey policies from KS 10.1.12.7 for group GDOI-G2 & gm identity 10.1.14.9 fvrf default ivrf default
GDOI-G2(config-if)#do sh crypto gdoi
GROUP INFORMATION
Group Name : GDOI-G2
Group Identity : 2
Group Type : GDOI (ISAKMP)
Crypto Path : ipv4
Key Management Path : ipv4
Rekeys received : 0
IPSec SA Direction : Both
Group Server list : 10.1.12.7
Group Member Information For Group GDOI-G2:
IPSec SA Direction : Both
ACL Received From KS : gdoi_group_GDOI-G2_temp_acl
Group member : 10.1.14.9 vrf: None
Local addr/port : 10.1.14.9/848
Remote addr/port : 10.1.12.7/848
fvrf/ivrf : None/None
Version : 1.0.12
Registration status : Registered
Registered with : 10.1.12.7
Re-registers in : 1097 sec
Succeeded registration: 1
Attempted registration: 8
Last rekey from : 0.0.0.0
Last rekey seq num : 0
Unicast rekey received: 0
Rekey ACKs sent : 0
Rekey Received : never
DP Error Monitoring : OFF
IPSEC init reg executed : 0
IPSEC init reg postponed : 0
Active TEK Number : 1
SA Track (OID/status) : disabled
allowable rekey cipher: any
allowable rekey hash : any
allowable transformtag: any ESP
Rekeys cumulative
Total received : 0
After latest register : 0
Rekey Acks sents : 0
ACL Downloaded From KS 10.1.12.7:
access-list deny udp any port = 848 any port = 848
access-list deny tcp any host 224.0.0.5
access-list deny tcp any host 224.0.0.6
access-list permit ip 10.1.12.0 0.0.0.255 10.1.14.0 0.0.0.255
KEK POLICY:
Rekey Transport Type : Unicast
Lifetime (secs) : 83974
Encrypt Algorithm : 3DES
Key Size : 192
Sig Hash Algorithm : HMAC_AUTH_SHA
Sig Key Length (bits) : 1296
TEK POLICY for the current KS-Policy ACEs Downloaded:
GigabitEthernet0/2:
IPsec SA:
spi: 0xA6F83D47(2801286471)
transform: esp-3des esp-sha-hmac
sa timing:remaining key lifetime (sec): (1176)
Anti-Replay(Counter Based) : 64
tag method : disabled
alg key size: 24 (bytes)
sig key size: 20 (bytes)
encaps: ENCAPS_TUNNEL
GDOI-G2(config-if)#
This seems pretty counter-intuitive. The ISAKMP profile is matching the loopback address, instead of the physical interface IP address on the GDOI-Server. surely, it would make more sense to match the interface that is sourcing the packets, right? Well, if you look at the linked blog post, there is no ISAKMP profile set, so do we need one? Let's remove it and find out:GDOI-G1(config)#no crypto map GDOI-G1 isakmp-profile GET-Profile
GDOI-G1(config)#no crypto isakmp profile GET-Profile
GDOI-G1(config)#end
GDOI-G2(config)#no crypto map GDOI-G2 isakmp-profile GET-Profile
GDOI-G2(config)#no crypto isakmp profile GET-Profile
GDOI-G2(config)#end
GDOI-Server#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.1.12.7 10.1.13.8 GDOI_IDLE 1025 ACTIVE
10.1.12.7 10.1.14.9 GDOI_IDLE 1027 ACTIVE
IPv6 Crypto ISAKMP SA
GDOI-Server#
GDOI-Server#sh crypto gdoi | i Name|Members
Group Name : GDOI-G1 (Unicast)
Group Members : 1
Profile Name : GET-Profile
Group Name : GDOI-G2 (Multicast)
Group Members : 1
Profile Name : GET-Profile
GDOI-Server#
So, less is more! Whilst we need an ISAKMP profile for Easy VPN, we don't need for GET VPN, and we didn't use it for DMVPN either. This is confirmed by reading this post from INE. this then begs the question, when do we use ISAKMP profiles?ISAKMP Profiles
ISAKMP profiles are used under these conditions:- When a router has two or more IPSec connections that have different Phase 1 parameters
- When using Easy VPN
- If different IKE v1 policies are used between different peers
- When using VRFs with different IKE Phase 1 parameters, but the same IP address.
ISAKMP profiles match peers on one or more attributes, such as address, hostname, username and so on. We can then use these to set different parameters, such as QoS groupings.
Here is the link (again) to the Cisco doc, with some useful scenario configurations for ISAKMP profiles.
Now that this is fixed, can we go back to hosting our GETVPN frm the loopback address?
GDOI-Server(config)#crypto gdoi group GDOI-G1
GDOI-Server(config-gkm-group)#server local
GDOI-Server(gkm-local-server)#sa ipsec 1
GDOI-Server(gkm-sa-ipsec)#address ipv4 7.7.7.7
GDOI-Server(gkm-sa-ipsec)
GDOI-Server(gkm-sa-ipsec)#crypto gdoi group GDOI-G2
GDOI-Server(config-gkm-group)#server local
GDOI-Server(gkm-local-server)#sa ipsec 1
GDOI-Server(gkm-sa-ipsec)#address ipv4 7.7.7.7
GDOI-Server(gkm-local-server)#
GDOI-G1(config)#crypto gdoi group GDOI-G1
GDOI-G1(config-gkm-group)#no server address ipv4 10.1.12.7
GDOI-G1(config-gkm-group)#server address ipv4 7.7.7.7
GDOI-G1(config-gkm-group)#
*Jul 6: %GDOI-4-GM_RE_REGISTER: The IPSec SA created for group GDOI-G1 may have expired/been cleared, or didn't go through. Re-register to KS.
*Jul 6: %CRYPTO-5-GM_REGSTER: Start registration to KS 7.7.7.7 for group GDOI-G1 using address 10.1.13.8 fvrf default ivrf default
*Jul 6: %CRYPTO-4-IKMP_NO_SA: IKE message from 7.7.7.7 has no SA and is not an initialization offer
*Jul 6: %GDOI-5-SA_TEK_UPDATED: SA TEK was updated
*Jul 6: %GDOI-5-SA_KEK_UPDATED: SA KEK was updated 0x6F792E443640770041679976AEFA1022
*Jul 6: %GDOI-5-GM_REGS_COMPL: Registration to KS 7.7.7.7 complete for group GDOI-G1 using address 10.1.13.8 fvrf default ivrf default
*Jul 6: %GDOI-5-GM_INSTALL_POLICIES_SUCCESS: SUCCESS: Installation of Reg/Rekey policies from KS 7.7.7.7 for group GDOI-G1 & gm identity 10.1.13.8 fvrf default ivrf default
GDOI-G1(config-gkm-group)#
GDOI-G2(config)#crypto gdoi grou GDOI-G2
GDOI-G2(config-gkm-group)#no server address ipv4 10.1.12.7
GDOI-G2(config-gkm-group)#server address ipv4 7.7.7.7
GDOI-G2(config-gkm-group)#
*Jul 6: %GDOI-4-GM_RE_REGISTER: The IPSec SA created for group GDOI-G2 may have expired/been cleared, or didn't go through. Re-register to KS.
*Jul 6: %CRYPTO-5-GM_REGSTER: Start registration to KS 7.7.7.7 for group GDOI-G2 using address 10.1.14.9 fvrf default ivrf default
*Jul 6: %GDOI-5-SA_TEK_UPDATED: SA TEK was updated
*Jul 6: %GDOI-5-GM_REGS_COMPL: Registration to KS 7.7.7.7 complete for group GDOI-G2 using address 10.1.14.9 fvrf default ivrf default
*Jul 6: %GDOI-5-GM_INSTALL_POLICIES_SUCCESS: SUCCESS: Installation of Reg/Rekey policies from KS 7.7.7.7 for group GDOI-G2 & gm identity 10.1.14.9 fvrf default ivrf default
GDOI-G2(config-gkm-group)#
GDOI-Server#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
7.7.7.7 10.1.13.8 GDOI_IDLE 1028 ACTIVE
7.7.7.7 10.1.14.9 GDOI_IDLE 1029 ACTIVE
IPv6 Crypto ISAKMP SA
GDOI-Server#sh crypto gdoi | i Name|Members
Group Name : GDOI-G1 (Unicast)
Group Members : 1
Profile Name : GET-Profile
Group Name : GDOI-G2 (Unicast)
Group Members : 1
Profile Name : GET-Profile
GDOI-Server#
Yes we can. It looks like the ISAKMP profile was stopping the ability to have the loopback address on the GDOI-Server as the pinpoint for the client VPNs, once this was fixed, everything works as it should.For our needs so far, we have not needed to use ISAKMP profiles, though, but that will change when we come to look at Easy VPN, which is up next.